Using TrueCrypt on Linux and Windows
Senin, 23 Desember 2013
0
komentar
http://dougvitale.wordpress.com/2013/11/18/using-truecrypt-on-linux-and-windows
After numerous revelations this year of the National Security Agency’s (NSA) frightening capabilities of mass spying on phone calls and Internet traffic (see, for example, PRISM), there has been a renewed interest in online privacy and the securing of our electronic data communications, such as Web and email activity. More and more Internet users are looking for solutions to keep their files, emails, and Web searches private. Help is not far off: one of the most effective ways to foil surveillance is by using encryption to make your data unreadable by other parties.
Data can be encrypted in two states – when it is in transmission through a communications network, or when it is at rest (i.e., stored on some sort of storage medium, such as a computer hard drive like the internal drive of your PC or an external USB flash drive). This blog has already covered SSH, RetroShare, and the Tor network as options for securing data in transit. Now we will look at TrueCrypt, perhaps the most popular solution for encrypting data at rest. This article will explain how TrueCrypt works and how you can utilize it on the two most popular operating systems, Microsoft Windows and Linux.

Jump to:
↑ Up to page menu
Boot loader: a small program (along with a small amount of needed data) stored in read-only memory (ROM) which accesses the nonvolatile device or devices from which the operating system programs and data can be loaded into RAM. (Wikipedia)
Hard disk drive: a data storage device used for storing and retrieving digital information using rapidly rotating disks (platters) coated with magnetic material. (Wikipedia)
Hidden operating system: an instance of an operating system (for example, Windows 7 or Windows XP) that is installed in a hidden TrueCrypt volume. (TrueCrypt)
Hidden volume: a TrueCrypt volume created within another TrueCrypt volume (within the free space on the volume). (TrueCrypt)
Key: the variable used by cryptographic processes to perform encryption and decryption (i.e., to transform plain text to cipher text and vice versa). (Wikipedia)
Keyfile: A file whose content is combined with a password. Until the correct keyfile is provided, no volume that uses the keyfile can be mounted. (TrueCrypt)
Master boot record (MBR): a special type of boot sector at the very beginning of partitioned computer mass storage devices (like fixed disks or removable drives) that holds the information on how the logical partitions, containing file systems, are organized on that medium. The MBR also contains executable code to function as a loader for the installed operating system, usually by passing control over to the loader’s second stage or in conjunction with each partition’s volume boot record. (Wikipedia)
Mounting a drive: For a hard disk or any partitions with filesystems on that disk to be accessible by a computer, they must first be mounted. The mounting process “activates” the disk/filesystem, making folders and files on the readable by the operating system. If a hard drive is physically connected to a computer but not mounted, it won’t be recognized. (Wikipedia)
Partition: a logical storage unit on a single physical disk drive. Multiple partitions can act like multiple disks so that different filesystems can be used on each partition. (Wikipedia)
Password: the string of characters you have to enter to access a TrueCrypt volume. Also called a passphrase.
Volume: a single accessible storage area (logical drive) with a single file system, typically (though not necessarily) resident on a single partition of a hard disk. (Wikipedia)
↑ Up to page menu
64-bit operating system:
$ wget http://www.truecrypt.org/download/truecrypt-7.1a-linux-x64.tar.gz
32-bit operating system:
$ wget http://www.truecrypt.org/download/truecrypt-7.1a-linux-x86.tar.gz
Now extract the installation file from the compressed tar file:
$ tar -zxvf truecrypt-7.1a-linux-x64.tar.gz
Then launch the installer file:
# ./truecrypt-7.1a-setup-x64
or
$ sudo ./truecrypt-7.1a-setup-x64
↑ Up to page menu
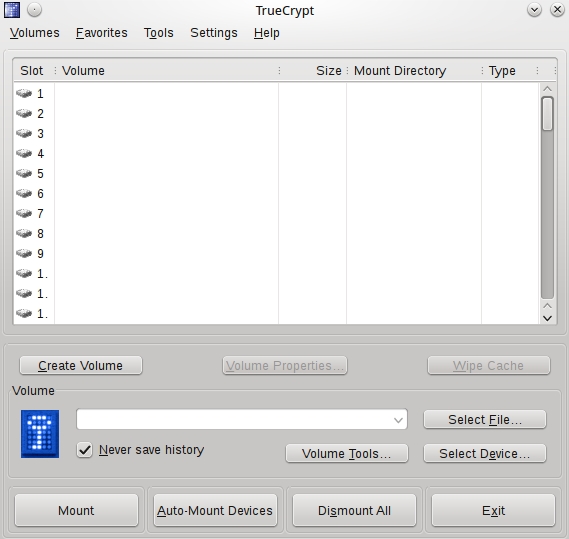
Here is the TrueCrypt interface for setting user preferences.
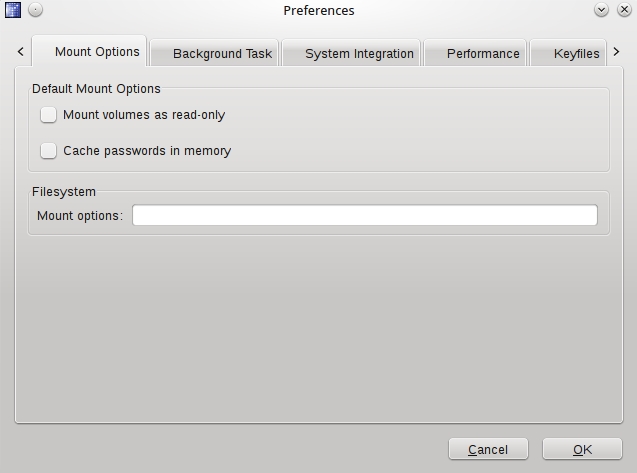
The simplest way to start benefiting from TrueCrypt’s capabilities is to launch the Volume Creation Wizard and let it guide you through the process of encrypting your files.
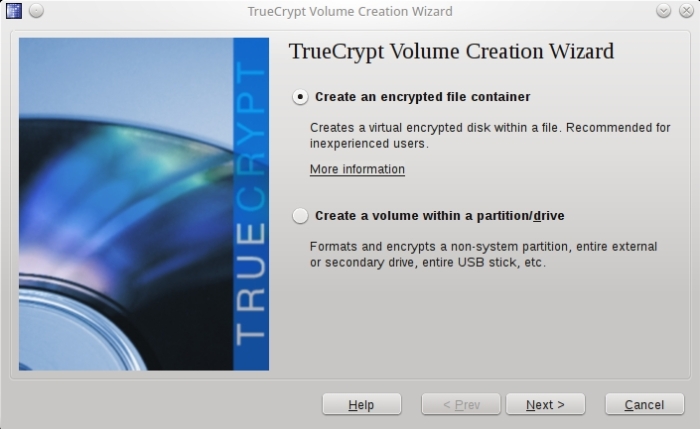
In Linux you also (not surprisingly) have the option to work with TrueCrypt from the non-graphical shell prompt using these command options.
truecrypt [OPTIONS] COMMAND
truecrypt [OPTIONS] VOLUME_PATH [MOUNT_DIRECTORY]
Create a new volume:
truecrypt -t -c
Mount a volume:
truecrypt volume.tc /media/truecrypt1
Mount a volume as read-only, using keyfiles:
truecrypt -m ro -k keyfile1,keyfile2 volume.tc
Mount a volume without mounting its filesystem:
truecrypt
Mount a volume prompting only for its password:
truecrypt -t -k “”
Dismount a volume:
truecrypt -d volume.tc
Dismount all mounted volumes:
truecrypt -d
If you experience problems trying to get TrueCrypt to work as desired on Linux, search for a solution in the Linux section of the official TrueCrypt discussion forum. You will need to create an account there to view and make posts.
↑ Up to page menu
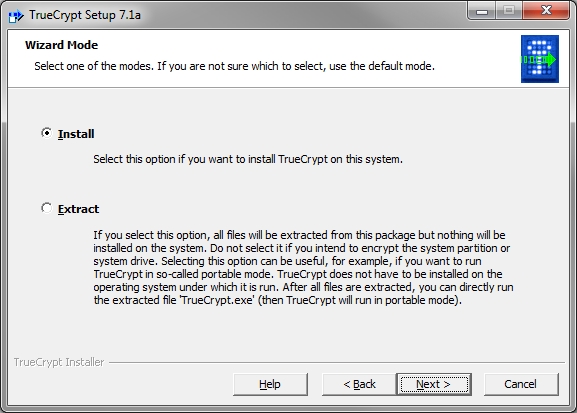
↑ Up to page menu
The Preferences interface on TrueCrypt for Windows is quite different from the Linux version.
You will also notice that the available options in the Volume Creation Wizard on Windows is different from what you see using Linux. Specifically, the option for “create a volume within a partition/drive” is absent; in its place are two others: “Encrypt a non-system partition/drive” and “Encrypt the system partition or entire system drive”. This discrepancy exists because “whole disk” system encryption is only available for the Windows OS.
The TrueCrypt Beginner’s Tutorial gives a step-by-step account of enabling disk encryption using the Windows GUI. If you experience problems trying to get TrueCrypt to work as desired on Windows, search for a solution in the official TrueCrypt discussion forum. You will need to create an account there to view and make posts.
truecrypt /q /v d:\myvolume
Dismount a volume mounted as the drive letter X (the main program window will not be displayed):
truecrypt /q /dx
Mount a volume called
truecrypt /v myvolume.tc /lx /a /p MyPassword /e /b
↑ Up to page menu
1. Can I be forced to provide my TrueCrypt password?
In the United Kingdom, if you do not do so you can be held criminally liable for such an offense as explained in these cases here, here, and here. US citizens should look closely at the Boucher case (decision (PDF); analysis), as well as the Judge Blackburn case in Colorado.
2. Why is TrueCrypt so difficult to crack?
Because it uses AES combined with PBKDF2 for key derivation. PBKDF2 is currently considered state of the art in passphrase expansion. It basically hashes the passphrase with a salt one thousand times to resist brute force attacks. The salt is an effective measure against rainbow tables.
3. Is there any way to defeat TrueCrypt?
Rather than defeating TrueCrypt’s cryptographic algorithms, it would be much easier to simply obtain the TrueCrypt password using illicit methods such as:
Have a look at Wikipedia’s comparison of disk encryption software.
↑ Up to page menu
Code.google.com, Cryptonite: EncFS and TrueCrypt on Android
Code.google.com, Truecrack brute-force password cracker for TrueCrypt
CryptographyEngineering.com, Let’s audit TrueCrypt (official Audit TrueCrypt)
Dailydot.com, Does being forced to decrypt a file violate the Fifth Amendment?
Delogrand.blogspot.fi, Extracting cached passphrases in Truecrypt
Github.com, TC-play TrueCrypt implementation
H-online.com, Attacking Truecrypt with TCHead
InfosecInstitute.com, Introduction to TrueCrypt
Media-addicted.de, Solid State Drives and TrueCrypt: durability and performance issues
Microsoft.com, CryptDB: Processing queries on an encrypted database (also CryptDB official)
Pingdom.com, How to secure your Google Drive with TrueCrypt (podcast)
Privacylover.com, Is there a backdoor in TrueCrypt?
Theregister.com, Brazilian banker’s crypto baffles the FBI
Truecrypt.org, TrueCrypt official FAQs
Volokh.com, 11th Circuit Finds 5th Amendment Right Against Self-Incrimination Protects Against Being Forced to Decrypt Hard Drive
YouTube.com, TrueCrypt on Kali Linux, TrueCrypt on Windows 7, and TrueCrypt on USB flash drives
ZDnet.com, Schneier research team cracks TrueCrypt (2008)
After numerous revelations this year of the National Security Agency’s (NSA) frightening capabilities of mass spying on phone calls and Internet traffic (see, for example, PRISM), there has been a renewed interest in online privacy and the securing of our electronic data communications, such as Web and email activity. More and more Internet users are looking for solutions to keep their files, emails, and Web searches private. Help is not far off: one of the most effective ways to foil surveillance is by using encryption to make your data unreadable by other parties.
Data can be encrypted in two states – when it is in transmission through a communications network, or when it is at rest (i.e., stored on some sort of storage medium, such as a computer hard drive like the internal drive of your PC or an external USB flash drive). This blog has already covered SSH, RetroShare, and the Tor network as options for securing data in transit. Now we will look at TrueCrypt, perhaps the most popular solution for encrypting data at rest. This article will explain how TrueCrypt works and how you can utilize it on the two most popular operating systems, Microsoft Windows and Linux.

Jump to:
- The basics of data-at-rest encryption
- TrueCrypt basics
- Installing TrueCrypt on Linux
- Using TrueCrypt on Linux
- Installing TrueCrypt on Windows
- Using TrueCrypt on Windows
- TrueCrypt tips and FAQs
- Further reference
- Recommended reading
The basics of data-at-rest encryption
While technologies such as Tor and SSL/TLS protect the confidentiality of your data as it passes through computer networks (especially the Internet), they do not offer protection of the files you have stored, such as on internal and external hard drives. If an unauthorized user obtains physical access to your PC, laptop, smart phone, or USB flash drive, what then? A popular IT security maxim is: If a bad guy has unrestricted physical access to your data, it’s not your data anymore – he owns it. If access to the files on these devices is not restricted by encryption, then the intruder can easily view them. Since most of us have files which we do not wish to share with anybody or with only a select few individuals, it is recommended to lock down your computer drives with a solution like TrueCrypt. TrueCrypt and similar tools obscure your files by converting them into unreadable code which, for all intents and purposes, is undecipherable without the required key. As a result, your files will be safe from prying eyes if physical security measures of your drives are compromised (e.g., if your devices are ever stolen or seized). Not only does TrueCrypt make it simple to implement data-at-rest encryption, it’s free and easy to obtain.↑ Up to page menu
TrueCrypt basics
Before you start to use TrueCrypt, you should be familiar with several terms which you will encounter when you install and configure it. These terms are:Boot loader: a small program (along with a small amount of needed data) stored in read-only memory (ROM) which accesses the nonvolatile device or devices from which the operating system programs and data can be loaded into RAM. (Wikipedia)
Hard disk drive: a data storage device used for storing and retrieving digital information using rapidly rotating disks (platters) coated with magnetic material. (Wikipedia)
Hidden operating system: an instance of an operating system (for example, Windows 7 or Windows XP) that is installed in a hidden TrueCrypt volume. (TrueCrypt)
Hidden volume: a TrueCrypt volume created within another TrueCrypt volume (within the free space on the volume). (TrueCrypt)
Key: the variable used by cryptographic processes to perform encryption and decryption (i.e., to transform plain text to cipher text and vice versa). (Wikipedia)
Keyfile: A file whose content is combined with a password. Until the correct keyfile is provided, no volume that uses the keyfile can be mounted. (TrueCrypt)
Master boot record (MBR): a special type of boot sector at the very beginning of partitioned computer mass storage devices (like fixed disks or removable drives) that holds the information on how the logical partitions, containing file systems, are organized on that medium. The MBR also contains executable code to function as a loader for the installed operating system, usually by passing control over to the loader’s second stage or in conjunction with each partition’s volume boot record. (Wikipedia)
Mounting a drive: For a hard disk or any partitions with filesystems on that disk to be accessible by a computer, they must first be mounted. The mounting process “activates” the disk/filesystem, making folders and files on the readable by the operating system. If a hard drive is physically connected to a computer but not mounted, it won’t be recognized. (Wikipedia)
Partition: a logical storage unit on a single physical disk drive. Multiple partitions can act like multiple disks so that different filesystems can be used on each partition. (Wikipedia)
Password: the string of characters you have to enter to access a TrueCrypt volume. Also called a passphrase.
Volume: a single accessible storage area (logical drive) with a single file system, typically (though not necessarily) resident on a single partition of a hard disk. (Wikipedia)
↑ Up to page menu
Installing TrueCrypt on Linux
Like all software meant for use on Linux, you should always check to see if TrueCrypt is available in your Linux distribution’s software repository. If it is, you can download and install it with your distro’s package manager, whether in a shell prompt or with a graphical user interface (GUI) such as Synaptic. If TrueCrypt is not available in this manner, you can proceed to the official download page and acquire the software in tar.gz format there. Alternatively, if you know the filename of the tar.gz file, you can use the wget download manager to acquire it via a shell prompt:64-bit operating system:
$ wget http://www.truecrypt.org/download/truecrypt-7.1a-linux-x64.tar.gz
32-bit operating system:
$ wget http://www.truecrypt.org/download/truecrypt-7.1a-linux-x86.tar.gz
Now extract the installation file from the compressed tar file:
$ tar -zxvf truecrypt-7.1a-linux-x64.tar.gz
Then launch the installer file:
# ./truecrypt-7.1a-setup-x64
or
$ sudo ./truecrypt-7.1a-setup-x64
↑ Up to page menu
Using TrueCrypt on Linux
When you launch TrueCrypt, you will see its main user interface.
Here is the TrueCrypt interface for setting user preferences.

The simplest way to start benefiting from TrueCrypt’s capabilities is to launch the Volume Creation Wizard and let it guide you through the process of encrypting your files.

In Linux you also (not surprisingly) have the option to work with TrueCrypt from the non-graphical shell prompt using these command options.
TrueCrypt command options (Linux) | Description |
|---|---|
truecrypt --auto-mount=devices|favorites | Auto mount device-hosted or favorite volumes. |
truecrypt --backup-headers[=VOLUME_PATH] | Backup volume headers to a file. All required options are requested from the user. |
truecrypt -c or --create[=VOLUME_PATH] | Create a new volume. Most options are requested from the user if not specified on command line. See also options --encryption, -k, --filesystem, --hash, -p, --random-source, --quick, --size, --volume-type. Note that passing some of the options may affect security of the volume (see option -p for more information).Inexperienced users should use the graphical user interface to create a hidden volume. When using the text user interface, the following procedure must be followed to create a hidden volume: 1) Create an outer volume with no filesystem. 2) Create a hidden volume within the outer volume. 3) Mount the outer volume using hidden volume protection. 4) Create a filesystem on the virtual device of the outer volume. 5) Mount the new filesystem and fill it with data. 6) Dismount the outer volume. If at any step the hidden volume protection is triggered, start again from step 1. |
truecrypt -C or --change[=VOLUME_PATH] | Change a password and/or keyfile(s) of a volume. Most options are requested from the user if not specified on command line. PKCS-5 PRF HMAC hash algorithm can be changed with option --hash. See also options -k, --new-keyfiles, --new-password, -p, --random-source. |
truecrypt --create-keyfile[=FILE_PATH] | Create a new keyfile containing pseudo-random data. |
truecrypt -d or --dismount[=MOUNTED_VOLUME] | Dismount a mounted volume. If MOUNTED_VOLUME is not specified, all volumes are dismounted. See below for description of MOUNTED_VOLUME. |
truecrypt --delete-token-keyfiles | Delete keyfiles from security tokens. See also command --list-token-keyfiles. |
truecrypt --display-password | Display password while typing. |
truecrypt --encryption=ENCRYPTION_ALGORITHM | Use specified encryption algorithm when creating a new volume. |
truecrypt --explore | Open explorer window for mounted volume. |
truecrypt --export-token-keyfile | Export a keyfile from a security token. See also command --list-token-keyfiles. |
truecrypt -f or --force | Force mounting of a volume in use, dismounting of a volume in use, or overwriting a file. Note that this option has no effect on some platforms. |
truecrypt --filesystem=TYPE | Filesystem type to mount. The TYPE argument is passed to the mount command with option -t. Default type is ‘auto’. When creating a new volume, this option specifies the filesystem to be created on the new volume (only ‘FAT’ and ‘none’ TYPE is allowed). Filesystem type ‘none’ disables mounting or creating a filesystem. |
truecrypt --fs-options=OPTIONS | Filesystem mount options. The OPTIONS argument is passed to mount with option -o when a filesystem on a TrueCrypt volume is mounted. This option is not available on some platforms. |
truecrypt -h or --help | Display detailed command line help. |
truecrypt --hash=HASH | Use specified hash algorithm when creating a new volume or changing password and/or keyfiles. This option also specifies the mixing pseudorandom function family (PRF) of the random number generator. |
truecrypt --import-token-keyfiles | Import keyfiles to a security token. See also option --token-lib. |
truecrypt -k or --keyfiles=KEYFILE1[,KEYFILE2,KEYFILE3,...] | Use specified keyfiles when mounting a volume or when changing password and/or keyfiles. When a directory is specified, all files inside it will be used (non-recursively). Multiple keyfiles must be separated by commas. Use double commas (,,) to specify a comma contained in keyfile’s name. Keyfile stored on a security token must be specified astoken://slot/SLOT_NUMBER/file/FILENAME. An empty keyfile (-k “”) disables interactive requests for keyfiles. See also options --import-token-keyfiles, --list-token-keyfiles, --new-keyfiles, --protection-keyfiles. |
truecrypt -l or --list[=MOUNTED_VOLUME] | Display a list of mounted volumes. If MOUNTED_VOLUME is not specified, all volumes are listed. By default, the list contains only volume path, virtualdevice, and mount point. A more detailed list can be enabled by the verbose output option (-v). |
truecrypt --list-token-keyfiles | Display a list of all available security token keyfiles. See also command --import-token-keyfiles. |
truecrypt --load-preferences | Load user preferences. |
truecrypt -m or --mount-options=OPTION1[,OPTION2,OPTION3,...] | Specifies comma-separated mount options for a TrueCrypt volume as follows: headerbak: Use backup headers when mounting a volume. nokernelcrypto: Do not use kernel cryptographic services. readonly|ro: Mount volume as read-only. system: Mount partition using system encryption. timestamp|ts: Do not restore host-file modification timestamp when a volume is dismounted (note that the operating system under certain circumstances does not alter host-file timestamps, which may be mistakenly interpreted to mean that this option does not work). See also option --fs-options. |
truecrypt --mount[=VOLUME_PATH] | Mount a volume interactively. Volume path and other options are requested from the user if not specified on command line. |
| truecrypt [MOUNTED_VOLUME] | Specifies a mounted volume. One of the following forms can be used: 1) Path to the encrypted TrueCrypt volume. 2) Mount directory of the volume’s filesystem (if mounted). 3) Slot number of the mounted volume (requires --slot). |
truecrypt --new-keyfiles=KEYFILE1[,KEYFILE2,KEYFILE3,...] | Add specified keyfiles to a volume. This option can only be used with command -C. |
truecrypt --new-password=PASSWORD | Specifies a new password. This option can only be used with command -C. |
truecrypt --non-interactive | Do not interact with the user. |
truecrypt -p or --password=PASSWORD | Use specified password to mount/open a volume. An empty password can also be specified (-p “”). Note that passing a password on the command line is potentially insecure as the password may be visible in the process list (see ps) and/or stored in a command history file or system logs. |
truecrypt --protect-hidden=yes|no | Write-protect a hidden volume when mounting an outer volume. Before mounting the outer volume, the user will be prompted for a password to open the hidden volume. The size and position of the hidden volume is then determined and the outer volume is mounted with all sectors belonging to the hidden volume protected against write operations. When a write to the protected area is prevented, the whole volume is switched to read-only mode. Verbose list (-v -l) can be used to query the state of the hidden volume protection. Warning message is displayed when a volume switched to read-only is being dismounted. |
truecrypt --protection-keyfiles=KEYFILE1[,KEYFILE2,KEYFILE3,...] | Use specified keyfiles to open a hidden volume to be protected. This option may be used only when mounting an outer volume with hidden volume protected. See also options -k and --protect-hidden. |
truecrypt --protection-password=PASSWORD | Use specified password to open a hidden volume to be protected. This option may be used only when mounting an outer volume with hidden volume protected. See also options -p and –protect-hidden. |
truecrypt --quick | Do not encrypt free space when creating a device-hosted volume. This option must not be used when creating an outer volume. |
truecrypt --random-source=FILE | Use FILE as a source of random data (e.g., when creating a volume) instead of requiring the user to type random characters. |
truecrypt --restore-headers[=VOLUME_PATH] | Restore volume headers from the embedded or an external backup. All required options are requested from the user. |
truecrypt --save-preferences | Save user preferences. |
truecrypt --size=SIZE | Use specified size in bytes when creating a new volume. |
truecrypt --slot=SLOT | Use specified slot number when mounting, dismounting, or listing a volume. |
truecrypt -t or --text | Use text user interface. Graphical user interface is used by default if available. This option must be specified as the first argument. |
truecrypt --test | Test internal algorithms used in the process of encryption and decryption. |
truecrypt --token-lib=LIB_PATH | Use specified PKCS #11 security token library. |
truecrypt -v or --verbose | Enable verbose output. |
truecrypt --version | Display program version. |
truecrypt --volume-properties[=MOUNTED_VOLUME] | Display properties of a mounted volume. |
truecrypt --volume-type=TYPE | Use specified volume type when creating a new volume. TYPE can be ‘normal’ or ‘hidden’. See option -c for more information on creating hidden volumes. |
TrueCrypt command line examples
Synopsis:truecrypt [OPTIONS] COMMAND
truecrypt [OPTIONS] VOLUME_PATH [MOUNT_DIRECTORY]
Create a new volume:
truecrypt -t -c
Mount a volume:
truecrypt volume.tc /media/truecrypt1
Mount a volume as read-only, using keyfiles:
truecrypt -m ro -k keyfile1,keyfile2 volume.tc
Mount a volume without mounting its filesystem:
truecrypt
--filesystem=none volume.tcMount a volume prompting only for its password:
truecrypt -t -k “”
--protect-hidden=no volume.tc /media/truecrypt1Dismount a volume:
truecrypt -d volume.tc
Dismount all mounted volumes:
truecrypt -d
If you experience problems trying to get TrueCrypt to work as desired on Linux, search for a solution in the Linux section of the official TrueCrypt discussion forum. You will need to create an account there to view and make posts.
↑ Up to page menu
Installing TrueCrypt on Windows
First head to the official TrueCrypt download page and download the setup file for Windows. When you launch the installer, you will be given the option to either perform a standard installation or just extract the contents of setup .exe file (if you choose the latter, you can copy the files to a USB Flash drive and run TrueCrypt in portable mode).
↑ Up to page menu
Using TrueCrypt on Windows
The TrueCrypt GUI on Windows is very similar to the Linux version. There are, however, a few interesting differences. First, in the main TrueCrypt GUI on Windows you can see that the first column is called “Drive” rather than “Slot”, and potential drive letters are shown rather than numbers.
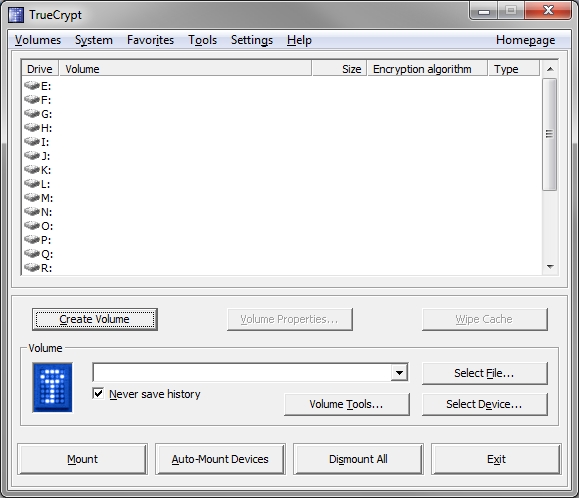
The Preferences interface on TrueCrypt for Windows is quite different from the Linux version.

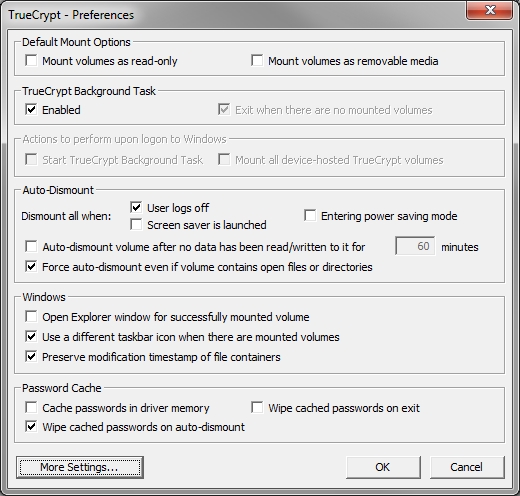
You will also notice that the available options in the Volume Creation Wizard on Windows is different from what you see using Linux. Specifically, the option for “create a volume within a partition/drive” is absent; in its place are two others: “Encrypt a non-system partition/drive” and “Encrypt the system partition or entire system drive”. This discrepancy exists because “whole disk” system encryption is only available for the Windows OS.

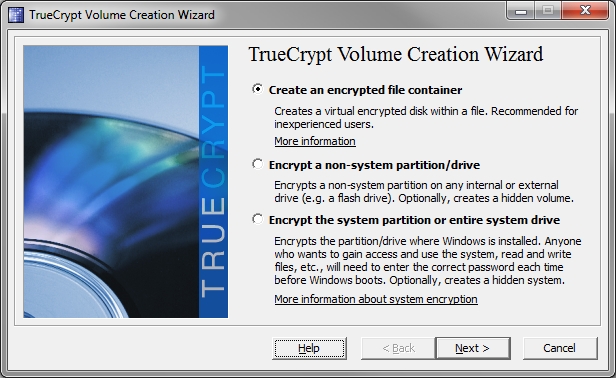
The TrueCrypt Beginner’s Tutorial gives a step-by-step account of enabling disk encryption using the Windows GUI. If you experience problems trying to get TrueCrypt to work as desired on Windows, search for a solution in the official TrueCrypt discussion forum. You will need to create an account there to view and make posts.
TrueCrypt command lines options on Windows
As in Linux, you can utilize TrueCrypt from a non-graphical command line environment if you wish. Sourced from the TrueCrypt Command Line Usage page.TrueCrypt.exe command options (Windows) | Description |
|---|---|
| truecrypt.exe /a or /auto [devices | favorites] | If no parameter is specified, automatically mount the volume. If devices is specified as the parameter, auto-mount all currently accessible device/partition-hosted TrueCrypt volumes. If favorites is specified as the parameter, auto-mount favorite volumes designated as “mount upon logon”. Note that /auto is implicit if /quit and /volume are specified. If you need to prevent the application window from appearing, use /quit. |
| truecrypt.exe /b or /beep | Beep after a volume has been successfully mounted or dismounted. |
| truecrypt.exe /c or /cache [y | n] | Enable or disable password cache, Note that turning the password cache off will not clear it (use /w to clear the password cache). |
| truecrypt.exe /d or /dismount [drive letter] | Dismount volume specified by drive letter. When no drive letter is specified, dismounts all currently mounted TrueCrypt volumes. |
| truecrypt.exe /e or /explore | Open a Windows Explorer window after a volume has been mounted. |
| truecrypt.exe /f or /force | Forces dismount (if the volume to be dismounted contains files being used by the system or an application) and forces mounting in shared mode (i.e., without exclusive access). |
| truecrypt.exe /h or /history [y | n] | Enables or disables saving the history of mounted volumes. |
| truecrypt.exe /help or /? | Display command line help. |
| truecrypt.exe /k or /keyfiles [keyfile | search path] | Specifies a keyfile or a keyfile search path. For multiple keyfiles, specify e.g.: /k c:\keyfile1.dat /k d:\KeyfileFolder /k c:\kf2. To specify a keyfile stored on a security token or smart card, use the following syntax: token://slot/SLOT_NUMBER/file/FILE_NAME. |
| truecrypt.exe /l or /letter [drive letter] | Driver letter to mount the volume as. When /l is omitted and when /a is used, the first free drive letter is used. |
| truecrypt.exe /m or /mount [bk|rm|recovery|ro|sm|ts] | bk or headerbak: Mount volume using embedded backup header. All volumes created by TrueCrypt 6.0 or later contain an embedded backup header (located at the end of the volume). recovery: Do not verify any checksums stored in the volume header. This option should be used only when the volume header is damaged and the volume cannot be mounted even with the mount option headerbak. rm or removable: Mount volume as removable medium. ro or readonly: Mount volume as read-only. ts or timestamp: Do not preserve container modification timestamp. sm or system: Without pre-boot authentication, mount a partition that is within the key scope of system encryption (for example, a partition located on the encrypted system drive of another operating system that is not running). Useful e.g. for backup or repair operations. Note: If you supply a password as a parameter of /p, make sure that the password has been typed using the standard US keyboard layout (in contrast, the GUI ensures this automatically). This is required due to the fact that the password needs to be typed in the pre-boot environment (before Windows starts) where non-US Windows keyboard layouts are not available. |
| truecrypt.exe format.exe /n or /noisocheck | Do not verify that TrueCrypt Rescue Disks are correctly burned. Warning: never attempt to use this option to facilitate the reuse of a previously created TrueCrypt Rescue Disk. Note that every time you encrypt a system partition/drive, you must create a new TrueCrypt Rescue Disk even if you use the same password. A previously created TrueCrypt Rescue Disk cannot be reused as it was created for a different master key. |
| truecrypt.exe /p or /password [password] | The volume password. If the password contains spaces, it must be enclosed in quotation marks (e.g., /p “My Password”). Use /p “” to specify an empty password. Warning: this method of entering a volume password may be insecure, for example, when an unencrypted command prompt history log is being saved to unencrypted disk. |
| truecrypt.exe /q or /quit [background|preferences] | Automatically perform requested actions and exit (main TrueCrypt window will not be displayed). If preferences is specified as the parameter (e.g.,/q preferences), then program settings are loaded/saved and they override settings specified on the command line. /q background launches the TrueCrypt Background Task (tray icon) unless it is disabled in the Preferences. |
| truecrypt.exe /s or /silent | If /q is specified, suppresses interaction with the user (prompts, error messages, warnings, etc.). If /q is not specified, this option has no effect. |
| truecrypt.exe /v or /volume [volume] | Path to a TrueCrypt volume to mount (do not use when dismounting). For a file-hosted volume, the path must include the filename. To mount a partition/device-hosted volume, use, for example, /v \Device\Harddisk1\Partition3 (to determine the path to a partition/device, run TrueCrypt and click ‘Select Device’). You can also mount a partition or dynamic volume using its volume name (for example, /v \\?\Volume{5cceb196-48bf-46ab-ad00-70965512253a}\). To determine the volume name use e.g. mountvol.exe. Also note that device paths are case-sensitive. |
| truecrypt.exe /w or /wipecache | Wipes any passwords cached in the driver memory. |
TrueCrypt.exe command line examples
Mount the volumed:\ myvolume as the first free drive letter, using the password prompt (the main program window will not be displayed):truecrypt /q /v d:\myvolume
Dismount a volume mounted as the drive letter X (the main program window will not be displayed):
truecrypt /q /dx
Mount a volume called
myvolume.tc using the password MyPassword, as the drive letter X. TrueCrypt will open an Explorer window and beep; mounting will be automatic:truecrypt /v myvolume.tc /lx /a /p MyPassword /e /b
↑ Up to page menu
TrueCrypt tips and FAQs
Tips:- Before installing and using TrueCrypt, do a complete backup of your data and make sure the backup is valid.
- When not using your device, shut it down. Do not simply lock the screen or go to sleep/hibernate mode.
- Use the hidden OS feature in case you compelled to reveal your password unwillingly. The official TrueCrypt site states:
When running, the hidden operating system appears to be installed on the same partition as the original operating system (the decoy system). However, in reality, it is installed within the partition behind it (in a hidden volume). All read/write operations are transparently redirected from the system partition to the hidden volume. Neither the operating system nor applications will know that data written to and read from the system partition is actually written to and read from the partition behind it (from/to a hidden volume). Any such data is encrypted and decrypted on the fly as usual (with an encryption key different from the one that is used for the decoy operating system).
- Glue up Firewire, Thunderbolt, PCMCIA, etc. ports to prevent DMA attacks. A DMA attack occurs when the attacker has physical access to the device and to memory address space via physical connections like Firewire and PCMCIA. These hardware connections interface directly to the OS kernel and therefore have complete access to RAM. Special purpose hardware devices can read and write arbitrary data to a computer’s memory, including encryption keys. Example attack on Macs. (Wikipedia).
1. Can I be forced to provide my TrueCrypt password?
In the United Kingdom, if you do not do so you can be held criminally liable for such an offense as explained in these cases here, here, and here. US citizens should look closely at the Boucher case (decision (PDF); analysis), as well as the Judge Blackburn case in Colorado.
2. Why is TrueCrypt so difficult to crack?
Because it uses AES combined with PBKDF2 for key derivation. PBKDF2 is currently considered state of the art in passphrase expansion. It basically hashes the passphrase with a salt one thousand times to resist brute force attacks. The salt is an effective measure against rainbow tables.
3. Is there any way to defeat TrueCrypt?
Rather than defeating TrueCrypt’s cryptographic algorithms, it would be much easier to simply obtain the TrueCrypt password using illicit methods such as:
- Evil maid attacks – occurs when an attack gains physical access to a target unbeknownst to the victim and installs malware such as keyloggers (Schneier).
- Cold boot attacks – extract the encryption keys from RAM while the computer is still running and data is in a decrypted state (Wikipedia).
- Rubber hose attacks – beating the person with a hose until they tell you the password, as shown here (Wikipedia).
Have a look at Wikipedia’s comparison of disk encryption software.
↑ Up to page menu
Further reference
16s.us, TCHunt Truecrypt volume locatorCode.google.com, Cryptonite: EncFS and TrueCrypt on Android
Code.google.com, Truecrack brute-force password cracker for TrueCrypt
CryptographyEngineering.com, Let’s audit TrueCrypt (official Audit TrueCrypt)
Dailydot.com, Does being forced to decrypt a file violate the Fifth Amendment?
Delogrand.blogspot.fi, Extracting cached passphrases in Truecrypt
Github.com, TC-play TrueCrypt implementation
H-online.com, Attacking Truecrypt with TCHead
InfosecInstitute.com, Introduction to TrueCrypt
Media-addicted.de, Solid State Drives and TrueCrypt: durability and performance issues
Microsoft.com, CryptDB: Processing queries on an encrypted database (also CryptDB official)
Pingdom.com, How to secure your Google Drive with TrueCrypt (podcast)
Privacylover.com, Is there a backdoor in TrueCrypt?
Theregister.com, Brazilian banker’s crypto baffles the FBI
Truecrypt.org, TrueCrypt official FAQs
Volokh.com, 11th Circuit Finds 5th Amendment Right Against Self-Incrimination Protects Against Being Forced to Decrypt Hard Drive
YouTube.com, TrueCrypt on Kali Linux, TrueCrypt on Windows 7, and TrueCrypt on USB flash drives
ZDnet.com, Schneier research team cracks TrueCrypt (2008)
TERIMA KASIH ATAS KUNJUNGAN SAUDARA
Judul: Using TrueCrypt on Linux and Windows
Ditulis oleh Unknown
Rating Blog 5 dari 5
Semoga artikel ini bermanfaat bagi saudara. Jika ingin mengutip, baik itu sebagian atau keseluruhan dari isi artikel ini harap menyertakan link dofollow ke http://androidjapane.blogspot.com/2013/12/using-truecrypt-on-linux-and-windows.html. Terima kasih sudah singgah membaca artikel ini.Ditulis oleh Unknown
Rating Blog 5 dari 5



0 komentar:
Posting Komentar