IPv6: how and why it enables Internet evolution
Minggu, 31 Maret 2013
0
komentar
http://dougvitale.wordpress.com/2013/03/28/ipv6-how-and-why-it-enables-internet-evolution
Internet Protocol version 6 (IPv6) is the next generation networking protocol that is slated to replace Internet Protocol version 4 (IPv4) as the dominant protocol powering modern computer networks and the global Internet.
The problem with IPv4 is that it was developed and initially rolled out in the 1970s and 80s, long before anyone had any idea of what the Internet would become (IPv4 is defined in RFC 791, published in 1981). Simply put, the ability for IPv4 to support modern Internet traffic is decreasing steadily. The Internet Engineering Task Force (IETF) recognized the potential for a crisis and commenced work on IPv4′s replacement in the mid-1990s.
The rest of this article will assume that you know why the Internet needs to evolve from IPv4 to IPv6. If you do not understand this, please stop reading and view this Youtube video of Vinton Cerf explaining the rationale behind the protocol migration (Cerf is considered one of the “fathers of the Internet”).
The death of IPv4 as a relevant networking protocol was delayed considerably by the deployment of two addressing-related solutions: Network Address Translation (NAT) and Classless InterDomain Routing (CIDR). However, given the current and projected growth in human population and the ever expanding quantity of devices connecting to the Internet, IPv6 is required to accommodate and sustain the necessary expansion of Internet availability and services. For example, two well-known technology growth sectors, mobile devices (e.g., smartphones) and cloud-based computing, require public IPv4 connectivity to function and therefore, they are contributing to the exhaustion of the public IPv4 address space (even with NAT relieving some pressure).
However, as IPv6 was developed from the ground up to be a future-oriented redesign and modernization of the IP structure, IT professionals will notice that it offers many distinct advantages over its aging cousin. Some noteworthy differences are:
Jump to:
IPv4 address example: 192.168.10.25
IPv6 address example: 2001:0DB8:124C:C1A2:BA03:6745:EF1C:683D
The increased bit count and the availability of 32 hexadecimal characters results in a significantly larger address space as compared to IPv4. IPv4 theoretically offers a maximum of 4,294,967,296 unique addresses, but certain address ranges are not allowed to be used for public addressing (such as 127.x.x.x, 10.x.x.x, 172.16.x.x, 192.168.x.x, etc.). So the real quantity of publicly available IPv4 addresses is considerably less than absolute limit of 4,294,967,296. IPv6, in contrast, offers the potential for such a large quantity of addresses that it is difficult to grasp. This number is 3.4×1038, resulting in a grand total of 340,282,366,920,938,463,463,374,607,431,768,211,456 possible addresses. This quantity is so huge that every star in the universe could have 340,282,366,920,938 universally unique IP addresses (the latest estimates are that there are 1022 to 1024 stars in existence). This means that each star would have a unique address space that is at least 80,000 thousand times greater than our current IPv4-based global Internet.
If you have experience with IPv4 subnetting, you are probably in the habit of being frugal with your address consumption. With IPv6, you can have so many subnets and hosts on each subnet that you no longer need to pinch IP addresses. IT professionals will need to make an effort to abandon the fear of using “too many IP addresses”. Believe it or not, you can simultaneously be wasteful with address space and have room to support future network growth. However, you will still need to follow sound IP addressing practices; i.e., do not simply toss IPv6 addresses around in a haphazard manner. Allocate them in logical, consistent, and meaningful ways (i.e., use patterns) and be sure to use an inventory tool to keep orderly records of address assignments (see IP Address Management tools on Wikipedia) as you are not likely to memorize IPv6 addresses. DNS will be even more of your friend than with IPv4.
The IPv4 addressing scheme includes network, subnet, and host divisions. IPv6, however, provides hierarchical addressing based on prefixes rather than the address classes of traditional IPv4. IPv6 addresses adhere to this format:
.
The global routing prefix is a hierarchically structured value assigned to a site. The subnet ID is an identifier of a link within the site. The interface ID is a unique identifier for a networked device on a given link (of course, multihomed devices have more than one interface).
As with IPv4 and its dotted decimal notation, it is important to understand IPv6 addresses not as they are commonly depicted (with hexadecimal characters) but as collections of bits. Here is IPv6 address 2001:DB8::2F3B:2AA:FF:FE28:9C5A in its “true” binary form:
As in IPv4, some of the bits in an IPv6 address stand for the network/subnet and the other bits stand for the host/interface. IPv6 does not use subnet masks (such as 255.255.192.0) but rather network prefixes to delineate the network/host boundary. Prefixes are all addresses that start with the same series of bits, and they are written in slash notation (such as /48). In other words, the prefix specifies how many of the leftmost contiguous bits of the address comprise the network. For example, the host address 29D0:14C7:4B92:9BD29:1A2B:E5F6:8C4D:1025/64 shows that the network prefix is the first 64 bits of the address (highlighted in bold). In other words, the network this host belongs to is 29D0:14C7:4B92:9BD29:0000:0000:0000:0000/64.
As another example, this is a 60-bit prefix (underlined): 14DE:0000:0000:BE50:0000:0000:0000:0000/60 (each hex digit is worth 4 bits, and fifteen digits are underlined). This prefix, 2001:0CD9::/32, contains all the interface addresses from 2001:0CD9:0000:0000:0000:0000:0000:0000 to 2001:0CD9:FFFF:FFFF:FFFF:FFFF:FFFF:FFFF. Similarly, prefix 2001:0CD9:1B3D::/48 contains all interface addresses from 2001:0CD9:1B3D:0000:0000:0000:0000:0000 to 2001:0CD9:1B3D:FFFF:FFFF:FFFF:FFFF:FFFF.
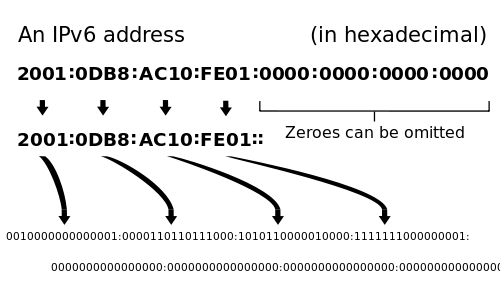
The first address in the paragraph above, 14DE:0000:0000:BE50:0000:0000:0000:0000/60, could be condensed to 14DE:0:0:BE50::/60. Unlike IPv4, addresses in IPv6 can be abbreviated to make them simpler to read and write. If an IPv6 address block (remember each address has 8 blocks) is comprised solely of 0s (zeroes), then it can be compressed into just one zero. In other words, address FE38:0000:124C:C1A2:BA03:6745:EF1C:683D could be written as FE38:0:124C:C1A2:BA03:6745:EF1C:683D. If there happen to be contiguous blocks of only 0s in an address, then these blocks can be omitted altogether. For example, FE38:0:0:0:BA03:6745:EF1C:683D could be represented as FE38::BA03:6745:EF1C:683D. This two-colon abbreviation may only be applied once in an address. Therefore, address FE00:0000:0000:0004:0000:0000:0000:0047 could be rewritten as FE00::4:0:0:0:47 or FE00:0:0:4::47, but not as FE00::4::47.
Organizations requesting IPv6 address allocations from their local regional Internet registry (RIR) are given address ranges with /48 prefixes. This means that the first three blocks (total of 48 bits) are fixed and do not change. Typically, organizations with a /48 range will then use the fourth block for the creation of subnets. So initially a /48 prefix is assigned, such as 2001:DB8:4B92::/48. Then the fourth block is populated to create subnets: 2001:DB8:4B92:xxxx::/64, where xxxx stands for hexadecimal digits 0000-FFFF. You should get used to seeing the /64 prefix length. Standard IPv6 addressing (specified in RFC 4291) requires that most unicast addresses use a 64-bit interface identifier. Additionally, this is a requirement of Stateless Address Auto Configuration (RFC 4862) and any network expecting SLAAC to occur must have a /64 prefix available.
A /64 prefix can provide for 18,446,744,073,709,551,616 addresses.
↑ Up to page menu
A unicast address is an identifier for a single interface. In other words, the final destination for packets sent to a unicast address is only to interface identified by that address.
A multicast address is an identifier for a group of interfaces. The intended final destination for packets sent to a multicast address is all the interfaces identified by that address. An interface may belong to several multicast address groups. Multicast addresses cannot function as source addresses, only destinations. The multicast entry on Wikipedia lists several instances in which hosts would transmit multicast rather than unicast data streams.
Like multicasts, an anycast address is an identifier for a group of interfaces. However, packets sent to anycast addresses are not delivered to all interfaces in that group. Instead, packets sent to an anycast address get delivered to the closest member of a group, according to the metric utilized by the routing protocol. In this way, anycasts are sort of like a hybrid between unicast and multicast addresses. The important point to remember is that packets sent to an anycast address will be delivered to one (and only one) of the nodes that are listening on that anycast address.
↑ Up to page menu
Global unicast addresses. These addresses can be regarded as the IPv6 equivalents of public IPv4 addresses. Global unicast addresses are publicly routable, globally unique, and the prefix 2000::/3 is designated for them (all addresses that begin with hexadecimal 2 or 3).
Link-local addresses. Used by autoconfiguration protocols like Neighbor Discovery Protocol (NDP), link-local addresses are automatically configured by IPv6 interfaces. Link-local addresses are used to communicate over a single physical or logical subnet, such as a typical Ethernet-based LAN. In this way, link-local addresses are similar to IPv4′s APIPA address range. APIPA is a feature of Microsoft Windows that acts as a DHCP failover mechanism (when a DHCP request or server fails, APIPA automatically allocates addresses in the private range 169.254.0.1 to 169.254.255.254).
The link-local default prefix is FE80::/10. Routers will not forward any packets to other links if the source or destination addresses are link-local.
Unique local addresses. Unique local addresses (ULAs) have replaced the deprecated site-local addresses which were previously standard in IPv6. Routers would not forward any packets to other sites if the source or destination addresses were site-local. ULAs are similar in that they are usually only routed within one site, but they can also be routed among a set of sites. However they are not to be routed globally (i.e., on the Internet) even though they are globally unique. Therefore you could join two subnets and not have to worry about IP address collisions.The standard ULA prefix is FC00::/7. Unique local addresses are similar to IPv4′s private (RFC 1918) address ranges.
The loopback address in IPv6 is 0:0:0:0:0:0:0:1/128, or ::1/128. As you recall, the IPv4 loopback address is 127.0.0.1/8. In both IPv6 and IPv4, the loopback address serves the same purposes. For instance, if you ping the loopback address and you receive replies, it’s a sign that TCP/IP protocol suite is properly functioning on the local host. To do this in IPv6, the command is
The unspecified address, 0:0:0:0:0:0:0:0/128 or ::/128, indicates the absence of an address and therefore cannot be assigned to any interface or used as a destination address. Instead it serves as the source address of any packets sent by an initializing host before it has learned its own proper IPv6 address. Ipv6 routers will not forward requests with the unspecified address as the source.
The loopback and unspecified addresses are established in RFC 4291.
IPv4-mapped IPv6 address. These unicast addresses are used by applications that transmit in IPv6 to allow them to talk with IPv4 hosts. The first 80 bits are zero, the next sixteen bits are 1, and the remaining 32 bits are the IPv4 address in dotted decimal notation. For example, ::FFFF:192.0.10.25 represents the IPv4 address 192.0.10.25. Standardized in RFC 4038.
IPv4-compatible IPv6 address. The IPv4-compatible address, 0:0:0:0:0:0:a.b.c.d (where a.b.c.d is the dotted decimal representation of an IPv4 address), is used by dual stack hosts to communicate using IPv6. When the IPv4-compatible address is used as an IPv6 destination, the IPv6 traffic is automatically encapsulated with an IPv4 header and sent to the destination using an IPv4 pathway. Example address: ::192.168.10.25. Deprecated since RFC 4291.
↑ Up to page menu
The following scopes apply to multicast addresses: interface-local (a single interface only), link-local (used by hosts when communicating with neighboring nodes on the same link), subnet-local (for subnets that span multiple links), admin-local (must be administratively configured), site-local (the site or organization network, not to be forwarded outside of scope), organization-local (intended to span multiple sites belonging to one organization), and global (globally unique, i.e. across the Internet).
Additionally there are a few defined types of multicast groups.
‘All nodes’ multicast groups
These groups identify all IPv6 nodes within a given scope.
These groups identify all IPv6 routers within a given scope.
Solicited-node multicast addresses are used by Neighbor Discovery Protocol for obtaining the Layer 2 addresses of other nodes (similar to ARP).
To avoid the possibility of SLAAC generating a duplicate link-local address, Duplicate Address Detection (DAD) is then invoked. This combination of IPv6 addresses generated from interface MAC addresses plus DAD means that collisions of link-local addresses are virtually no longer a concern. This news will come as a relief for any network administrators who have ever had to merge two or more subnets that used addressing schemes in, for example, the 192.168.x.x or 10.x.x.x ranges.
Like DHCP in IPv4, IPv6 hosts can also be configured to acquire connectivity parameters from DHCPv6 servers. IPv4 clients use DHCP broadcasts to locate DHCP servers, and since broadcasts are extinct in IPv6, clients use specialized multicasts to locate DHCPv6 servers. These multicasts use the reserved address FF02::1:2. One notable difference between DHCP and DHCPv6 is that while DHCP can inform clients which node to use as the default gateway, DHCPv6 does not do this. The default gateway should be a link-local router that can reliably make its own existence known via router advertisements. So IPv6 clients must be informed of the default gateway address via the SLAAC process. Another difference between DHCP and DHCPv6 is that while DHCP is a very “tried and true” service, DHCPv6 did not perform very well in a 2011 vendor-neutral interoperability test.
↑ Up to page menu
However, like all new technologies, IPv6 will not be free of vulnerabilities. There will definitely be bugs found in its underlying code, and as the protocol becomes more and more diffused throughout global networks, security holes will surely be discovered. Indeed, although IPv6 is just at the dawn of its eventual worldwide deployment, there has already been a considerable quantity of IPv6 vulnerabilities discovered in recent years. Websites that track computing vulnerabilities have catalogued numerous IPv6 holes and exploits, and many more protocol weaknesses will be uncovered in coming years. For listings of the vulnerabilities published so far, you can visit:
IPv6 should definitely not be regarded as a miraculous cure-all that will immediately reduce network vulnerabilities and threat vectors. The same basic threats and respective security measures and guidelines apply to both IPv4 and IPv6. For example, even though IPv6 is better suited to resist scanning of address blocks as previously mentioned, targeted scanning scanning and probing against specific hosts is still very much possible. Packet sniffing is also still a valid threat. Such security concerns should serve to motivate organizations to to transition to IPv6 sooner rather than later because a hastily deployed IPv6 network is one which will not be as locked down as its IPv4 counterpart or predecessor. Therefore it’s advisable to upgrade to IPv6 when there is plenty of time to spare for testing and gradual deployment.
Most networks today already have many IPv6-enabled hosts, including every node running Windows Vista, Windows 7, Mac OS/X, and all modern Linux, Unix, and BSD. These hosts can use SLAAC as previously described to communicate with other IPv6 network devices and services on the same LAN, and if they can contact an IPv6-enabled router then there may be unapproved, “rogue” IPv6 traffic on your network which could evade IPv4-based security measures. Even though the built-in Windows Firewall is compatible with IPv6, Windows hosts have the potential to be particularly worrisome because they do not support two IETF security standards:
An attack tool targeting IPv6, THC-IPv6, is available for download for use by hackers and ethical hackers alike. There are, however, a few programs that can help secure your IPv6 hosts. One is NDPMon, which can detect suspicious ICMPv6 traffic. Another is 6Guard, which is specifically designed to counter THC-IPv6.
Now that Nmap is compatible with IPv6, there are a handful of Nmap scripts that can be used to assess IPv6 hosts.
↑ Up to page menu
Functionally speaking, NAT can be seen as a sort of “hack” solution for networks because all ingress and egress packets are examined and altered, thereby introducing extra complexity and hence, more potential for erroneous configurations and bugs. Wikipedia’s entries on NAT and NAT traversal explain NAT’s disadvantages and drawbacks in more detail. As Iljitsch van Beijnum states on ArsTechnica:
↑ Up to page menu
When you decide to enable and support IPv6, many standard network security considerations will apply. For instance, the IPv4-based access control lists (ACLs) on your network perimeter must be coupled with new IPv6 ACLs that offer the same level of protection. On the client side, most operating systems released in the 21st century are equipped to handle IPv6. If a modern version of Linux or Windows boots up and detects an IPv6 router on the LAN that advertises an IPv6 prefix, it will generate an IPv6 address. This functionality will surely prove beneficial during IPv4-to-IPv6 network upgrades because many hosts will remain online and users will be able to continue working. However, this also means that there could be unapproved, covert IPv6 traffic traversing your network.
Many respected and influential enterprises have already made the decision to embrace IPv6. Google, for instance, has already acquired a tremendous amount of IPv6 addresses. Google owns every address with the prefix 2001:4860::/32. Google has also deployed public IPv6 DNS servers (2001:4860:4860::8888 and 2001:4860:4860::8844). Other major industry giants such as Microsoft, Cisco, Juniper, Red Hat, Verizon, Sprint, AT&T, Comcast, Netgear, D-Link, and Belkin have also rallied to the call to roll out IPv6 services.
Complicating the deployment of IPv6 is the fact that (quite regrettably) IPv4 and IPv6 are not directly compatible. In other words, hosts connecting solely over IPv4 cannot directly communicate with hosts connected solely via IPv6. In response to this challenge, several interprotocol transition solutions have been developed. These transition technologies are mechanisms designed to enable service providers and network operators to migrate their subscriber base (users) from IPv4 to IPv6. In the ideal interim transition environment, both IPv4 and IPv6 are fully deployed across all the infrastructure, meaning that all networked hosts (such as servers, workstations, mobile devices, etc.) and all networking devices (such as routers, switches, firewalls, etc.) can process both IPv4 and IPv6. Additionally all content, applications, and services are available via both protocols. To end users, however, the utilization of two different protocols should remain transparent. In the ideal end state environment, IPv6 has fully replaced IPv4 and all nodes communicate solely via IPv6.
One undesirable side effect of these transition methods is that they may end up actually delaying the transition from IPv4 to IPv6. Remember, the idea is to get weaned off IPv4, not to artificially prolong its lifespan. It is quite unfortunate that IPv6 is almost twenty years old but has yet to achieve widespread adoption, particularly in the USA. One very positive outcome of rolling out IPv6 is that such a protocol upgrade is a one-time deal…you and/or your successors will never have to worry about undergoing a similar process for a long, long time. If the estimated lifespan of IPv4 ends up being about fifty years (it was standardized in 1981), then it’s very likely that IPv6 will exist as a viable networking protocol for hundreds of years after we are gone.
The three main types of transition mechanisms are:
Typically NAT is performed by customer premises equipment (CPE) such as your home or business router. When service providers deploy NAT gear for IPv6-IPv4 translation, this practice is known as Large Scale NAT (LSN) or Carrier-Grade NAT (CGN).
NAT64 and NAT46 are described in more detail by this IETF draft. The NAT64 protocol specification can be found in RFC 6146. IPv6/IPv4 translation as a whole is discussed in RFC 6144.
6to4
6to4, Teredo, and ISATAP are automatic tunneling techniques. 6to4 uses a default relay tunnel address, 192.88.99.x and a default gateway of 192.88.99.1. Any traffic directed to this IPv4 address range is probably carrying encapsulated 6to4 IPv6 traffic (6to4 packets start with 2002::/16). 6to4 works well when a 6to4 router exists at the edge of the site. The 6to4 router uses a public IPv4 address to construct the 6to4 prefix and encapsulates and decapsulates IPv6 traffic sent to and from nodes in the site. So, 6to4 needs configuration of a public IPv4 address and the implementation of 6to4 routing functionality on the site’s edge device. Many small office/home office (SOHO) configurations use an IPv4 NAT device for Internet connectivity. In most NAT configurations, the device providing NAT functionality is not capable of acting as a 6to4 router. Even if 6to4 were universally supported in Internet edge devices, there are some Internet connectivity configurations that contain multiple levels of NATs.
Teredo solves the issues of the lack of 6to4 functionality in modern-day Internet edge devices and multilayered NAT configurations by tunneling IPv6 packets between the hosts within the sites. In contrast, 6to4 tunnels IPv6 packets between the edge devices. Teredo allows IPv6 connectivity between IPv6 and IPv4 nodes that are separated by one or more NAT devices. Teredo traffic is composed of IPv6 packets that have been encapsulated as IPv4-based UDP messages, and UDP can be translated universally by NAT devices and can traverse multiple NAT layers. Teredo functionality is explained more thoroughly in Technet’s Teredo overview (Teredo was developed by Microsoft). Teredo is also described in RFC 4380.
6rd
6RD has a lot in common with 6to4. 6to4 works by relaying traffic between native IPv6 and IPv4 using relay servers which advertise common IPv4 and IPv6 prefixes to networks they are prepared to provide relay services for, but there is no guarantee that all native IPv6 hosts have a working route toward such a relay. With 6rd, this model is changed by making each ISP use one of its own IPv6 prefixes instead of the special 2002::/16 prefix standardized for 6to4. The 6rd protocol specification can be found in RFC 5969.
6in4 is the encapsulation of IPv6 packets in IPv4 packets. In 6in4, the IPv4 packet header is immediately followed by the IPv6 packet. This means that the encapsulation overhead is simply the size of the IPv4 header (20 bytes) which avoids MTU packet fragmentation. More details can be found in RFC 4213.
6over4
6over4 is a transition mechanism which allows isolated IPv6 hosts, located on a physical link which has no directly connected IPv6 router, to use an IPv4 multicast domain as their virtual local link. A 6over4 host uses an IPv4 address for the interface in the creation of the IPv6 interface ID, placing the 32-bit IPv4 address in the low order bits and padding to the left with 0′s for a total of 64 bits. The IPv6 prefix used is the normal IPv6 prefix, and can be manually configured or dynamically learned by way of SLAAC.
6over4 is officially documented in RFC 2529. Semantic differences between the terms “6in4″ and “6over4″ are addressed in a 2005 IETF draft document.
6PE
Cisco’s IPv6 Provider Edge (6PE) is a tunneling solution for MPLS backbones.
Dual Stack Lite (DS-Lite) uses 4in6 tunnels to send traffic to a DS-Lite server which then NATs the traffic though a tunnel. This allows for IPv6-only connections between the customer site and the service provider’s Large Scale NAT (LSN), but instead of translating from IPv4 to IPv6 as in NAT464, the IPv4 packets are tunneled to the LSN, so no translation needs to be performed. More info on DS-Lite can be found here and here. Standard specification is in RFC 6333.
Dual Stack Transition Mechanism (DSTM) encapsulates IPv4 packets within IPv6 (4in6). Standard specification can be found on IETF.org. DSTM is designed to rapidly reduce the reliance on IPv4 routing and is intended for IPv6-only networks in which hosts still occasionally need to communicate directly with other IPv4 hosts.
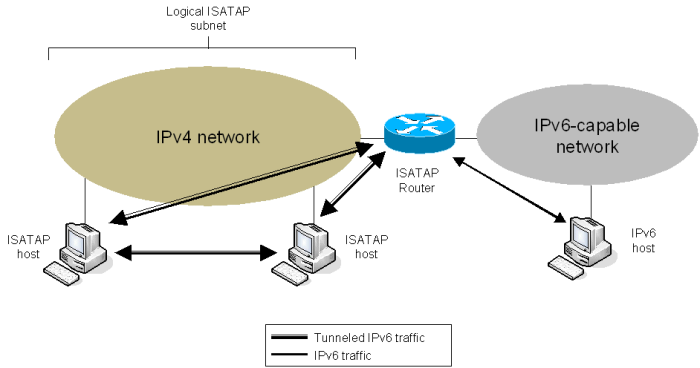
ISATAP
Intra-site Automatic Tunnel Addressing Protocol (ISATAP). Unlike 6to4 tunnels, ISATAP tunnels do not work if IPv4 NAT is used between the tunnel endpoints. The IETF describes ISATAP in RFC 5214.
In the Red Hat Linux family (which includes Fedora and CentOS), open up the
The second step is to open
Now enter the command:
For Debian-based Linuxes (including Ubuntu and Mint), open
Then open
Now enter the command:
IPv6 traffic blocking and filtration in Linux is possible with the ip6tables firewall. On your firewall host, issue the command
If you want to configure a Linux host to act as an IPv6-capable router, you must enable the Router Advertisement Daemon (RADVD). RADVD listens for Router Solicitations (RS) and responds with Router Advertisement (RA) replies. This is the same process as described in the IP address acquisition section above. You can tweak RADVD’s parameters in
Linux clients can utilize Teredo tunneling courtesy of the Miredo tunneling client.
Be sure to have a look at the ‘IPv6 and Linux’ links below.
↑ Up to page menu
With a little effort, IPv6 can be installed and enabled on Windows XP and Windows Server 2003. To install IPv6 on Windows XP, open up a command prompt and type:
Instructions to install, configure, and uninstall IPv6 on Windows Server 2003 can be found here and here.
In Windows XP and Windows Server 2003, the IPv6 interface ID is derived from the Extended Unique Identifier (EUI)-64 address. In Windows Vista and Windows Server 2008, the interface ID by default is randomly derived, rather than based on the EUI-64 address. You can disable random interface IDs with the
IPv6 in Windows XP and Windows Server 2003 uses the Automatic Tunneling Pseudo-Interface for encapsulating IPv6 packets with an IPv4 header so that they can be transmitted across an IPv4 network. By default, IPv6 configures a link-local Intra-Site Automatic Tunnel Addressing Protocol (ISATAP) address on the Automatic Tunneling Pseudo-Interface. The link-local ISATAP address has the form
To specify your IPv6 address parameters in Windows, click the System Menu, Control Panel, Network and Sharing Center, and then Change Adapter Settings. Now right-click your network interface and choose Properties. Highlight ‘Internet Protocol Version 6 (TCP/IPv6)’ and click Properties.
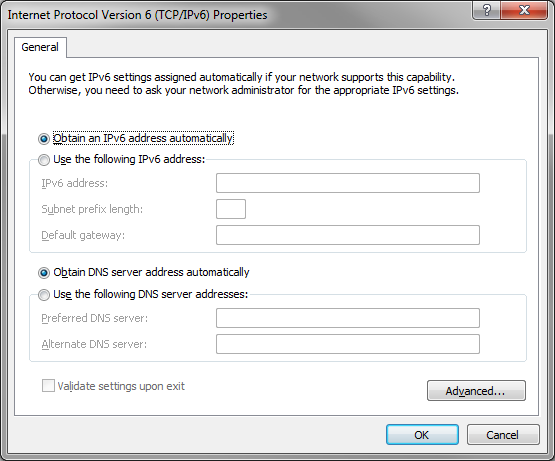
.
Be sure to have a look at the ‘IPv6 and Microsoft’ links below.
↑ Up to page menu
6deploy.eu, Collection of IPv6 tutorials in PDF format
Afrinic.net, IPv6 virtual lab
Brighttalk.com, IPv6 on your network (webcast)
CIO.gov, Planning guide/roadmap toward IPv6 adoption within the U.S. government
Code.google.com, IPv6gen prefix generator
Deepspace6.net, ipv6calc
GetIPv6.info (ARIN), IPv6 presentations and documents
Google.com, IPv6 adoption statistics
HE.net, Porting applications from IPv4 to IPv6/IPv4 dual stack
Hpc.hpcmo.mil, Lessons learned after deploying IPv6 (from multiple organizations)
Icann.org, Testing firewalls for IPv6 and EDNS0 support
InfoSecInstitute.com, IPv6 surface analyzer
Internet2.edu, Internet2 IPv6 Working Group
Internetsociety.org, Deploy360 IPv6 resources
Ipbcop.org, Recommendations for IPv6 subnetting guidelines
IPv6tf.org, IPv6 For All (PDF; contains numerous real world examples of configuring IPv6 on various technologies)
IPv6-test.com, IPv6 connectivity test
Isc.sans.edu, IPv4-to-6to4 converter
Networkworld.com, IPv6 networking certifications
Networkworld.com, What if IPv6 fails to catch on?
Routermeister.net, Sipcalc IPv6 subnet calculator
Sixxs.net, Table comparing IPv6 transition methods
Sourceforge.net, HaCi IPv6 address administration tool
Surfnet.nl, Preparing and IPv6 addressing plan
Test-ipv6.com, IPv6 connectivity test
Wikipedia.org, Collection of IPv6 Address Management (IPAM) tools
Youtube.com, DEFCON 18: Who cares about IPv6?
IPv6 and security
Brighttalk.com, IPv6 requires fundamental change to vulnerability management programs (webcast)
Brighttalk.com, IPv6 – security threat or stronger defenses? (webcast)
InfoSecInstitute.com, SLAAC attack on Windows default IPv6 configuration
InfoSecInstitute.com, Security vulnerabilities of IPv6 tunnels
NIST.gov, Special Publication (SP) 800-119, Guidelines for the secure deployment of IPv6 (PDF)
Technet.microsoft.com, IPv6 security considerations and recommendations
Youtube.com, Recent advances in IPv6 insecurities
IPv6 and Cisco
Cisco.com, Enterprise IPv6 solution data sheets, presentations, and white papers
Cisco.com, IPv6: A service provider view in advancing MPLS networks
Cisco.com, IPv6 access control lists (ACLs)
Cisco.com, IPv6 network mobility
Cisco.com, IPv6 site multihoming
Cisco.com, IPv6 worldwide adoption statistics
Proprofs.com, CCNA IPv6 flash card questions
IPv6 and Linux
HE.net, Essential IPv6 for Linux system administrators (PDF)
Linux.com, IPv6 crash course for Linux and Another IPv6 crash course for Linux
TLDP.org, Linux IPv6 HOWTO
Youtube.com, Essential IPv6 for Linux system administrators (video)
IPv6 and Microsoft
Technet.microsoft.com, Changes to IPv6 in Windows Vista and Windows Server 2008
Technet.microsoft.com, How IPv6 works
Technet.microsoft.com, IPv6 for Windows frequently asked questions (FAQs)
Technet.microsoft.com, IPv6 forum
Technet.microsoft.com, IPv6 survival guide
Technet.microsoft.com, Support for IPv6 in Windows Server 2008 R2 and Windows 7
Zdnet.com, Windows 8 moves to IPv6 Internet
Notable IPv6-related IETF Requests For Comments (RFCs)
RFC 2080, RipNG for IPv6
RFC 2460, Internet Protocol Version 6 Specification
RFC 2461, Neighbor Discovery for IP Version 6 (IPv6)
RFC 2462, IPv6 Stateless Address Autoconfiguration
RFC 2473, Generic Packet Tunneling in IPv6 Specification
RFC 2528, Transmission of IPv6 over IPv4 Domains without Explicit Tunnels
RFC 3056, Connection of IPv6 Domains Via IPv4 Clouds (6to4)
RFC 3152, DNS Extensions to Support IP Version 6
RFC 3162, RADIUS for IPv6
RFC 3315, Dynamic Host Configuration Protocol Version 6
RFC 3375, Mobility Support in IPv6
RFC 3587, IPv6 Global Unicast Address Format
RFC 4007, IPv6 Scoped Address Architecture
RFC 4038, Application Aspects of IPv6 Transition
RFC 4213, Basic Transition Mechanisms for IPv6 Hosts and Routers
RFC 4291, IP Version 6 Addressing Architecture
RFC 4294, IPv6 Node Requirements
RFC 4380, Teredo: Tunneling IPv6 over UDP through Network Address Translations (NATs)
RFC 4862, IPv6 Stateless Address Autoconfiguration
RFC 5156, Special-Use IPv6 Addresses
RFC 5214, Intra-Site Automatic Tunnel Addressing Protocol (ISATAP)
RFC 5340, OSPF for IPv6
RFC 5533, Shim6: Level 3 Multihoming Shim Protocol for IPv6
RFC 5881, BFD for IPv4 and IPv6 (Single Hop)
RFC 5902, IAB Thoughts on IPv6 Network Address Translation
RFC 5952, A Recommendation for IPv6 Address Text Representation
RFC 5969, IPv6 Rapid Deployment on IPv4 Infrastructures (6rd)
RFC 5991, Teredo Security Updates
RFC 6052, IPv6 Addressing of IPv4/IPv6 Translators
RFC 6081, Teredo Extensions
RFC 6092, Recommended Simple Security Capabilities in Customer Premises Equipment (CPE) for Providing Residential IPv6 Internet Service
RFC 6144, Framework for IPv4/IPv6 Translation
RFC 6146, Stateful NAT64: Network Address and Protocol Translation from IPv6 Clients to IPv4 Servers
RFC 6177, IPv6 Address Assignment to End Sites
RFC 6296, IPv6-to-IPv6 Network Prefix Translation
RFC 6333, Dual-Stack Lite Broadband Deployments Following IPv4 Exhaustion
RFC 6540, IPv6 Support Required for All IP-Capable Nodes
RFC 6586, Experiences from an IPv6-Only Network
RFC 6724, Default Address Selection for Internet Protocol Version 6 (IPv6)
Internet Protocol version 6 (IPv6) is the next generation networking protocol that is slated to replace Internet Protocol version 4 (IPv4) as the dominant protocol powering modern computer networks and the global Internet.
The problem with IPv4 is that it was developed and initially rolled out in the 1970s and 80s, long before anyone had any idea of what the Internet would become (IPv4 is defined in RFC 791, published in 1981). Simply put, the ability for IPv4 to support modern Internet traffic is decreasing steadily. The Internet Engineering Task Force (IETF) recognized the potential for a crisis and commenced work on IPv4′s replacement in the mid-1990s.
The rest of this article will assume that you know why the Internet needs to evolve from IPv4 to IPv6. If you do not understand this, please stop reading and view this Youtube video of Vinton Cerf explaining the rationale behind the protocol migration (Cerf is considered one of the “fathers of the Internet”).
The death of IPv4 as a relevant networking protocol was delayed considerably by the deployment of two addressing-related solutions: Network Address Translation (NAT) and Classless InterDomain Routing (CIDR). However, given the current and projected growth in human population and the ever expanding quantity of devices connecting to the Internet, IPv6 is required to accommodate and sustain the necessary expansion of Internet availability and services. For example, two well-known technology growth sectors, mobile devices (e.g., smartphones) and cloud-based computing, require public IPv4 connectivity to function and therefore, they are contributing to the exhaustion of the public IPv4 address space (even with NAT relieving some pressure).

Image source: Wikimedia Commons
Despite their differences in age, IPv4 and IPv6 do share some characteristics. Both protocols were designed to allow for host identification, host discovery, and optimal routing. They both work at Layer 3 of the OSI networking model and at the internet layer of the TCP/IP networking model. In order for hosts to properly communicate using IPv4 or IPv6, they must be assigned a unique IP address. IPv6 hosts need the same information as IPv4 hosts to properly network, e.g., they need to know the IP addresses of DNS servers (to translate host names to IP addresses) and default gateways (to transmit to remote destinations). As in IPv4, IPv6 hosts will send packets directly to destinations on the same subnet.However, as IPv6 was developed from the ground up to be a future-oriented redesign and modernization of the IP structure, IT professionals will notice that it offers many distinct advantages over its aging cousin. Some noteworthy differences are:
- IP addressing – as described below, IPv6 addresses use a different format and can provide an astonishingly huge address space for network hosts, far larger than what IPv4 can offer.
- Multicast and broadcast – IPv6 utilizes more multicast traffic while dropping broadcast functionality altogether.
- Multi-address interfaces – In IPv6, interfaces (such as network interface cards, or NICs) can natively operate using several IP addresses. IPv6 offers improved support for multiple addresses sharing one interface.
- Automatic IP address assignment – While IPv4 clients can receive address assignments via DHCP, IPv6 hosts are capable of autoconfiguration with stateless address autoconfiguration (SLAAC) via Neighbor Discovery Protocol (NDP). Alternatively, IPv6 hosts can utilize the new DHCPv6 in a manner similar to traditional DHCP.
- Packet fragmentation – Routers processing IPv6 will not fragment packets. Instead, fragmentation responsibility belongs to the originating hosts.
- Checksum – the IPv6 header does not include a checksum while IPv4 does. Removing the checksum from OSI Layer 3 should improve IP throughput.
- Layer 2 (data link) address discovery – while IPv4 uses Address Resolution Protocol (ARP), IPv6 uses ICMPv6-based Neighbor Discovery Protocol (NDP).
- IPSec – IPSec support is optional in IPv4 but is required in IPv6.
- IGMP – IPv6 replaces Internet Group Management Protocol (IGMP) with Multicast Listener Discovery (MLD).
Jump to:
- IPv6 address format
- IPv6 address types
- IPv6 unicast address types
- IPv6 multicast address types
- IPv6 reserved prefixes
- IPv6 automatic address acquisition by hosts
- IPv6 and traditional NAT
- IPv6 and security
- IPv4-to-IPv6 transition methods
- Configuring IPv6 on Linux
- Configuring IPv6 on Windows
- Further reference
- Recommended reading
IPv6 address format
As described in my IPv4 subnetting article, IPv4 utilizes addresses that are 32 bits in length and comprised of four distinct fields (called octets). Each octet contains a value of eight bits. IPv6, however, uses 128-bit addresses. These 128-bit addresses take the form of eight hexadecimal fields (or blocks) that are separated by colons. Each block is sixteen bits in size and is represented by four hexadecimal characters (0-9 and A-F).IPv4 address example: 192.168.10.25
IPv6 address example: 2001:0DB8:124C:C1A2:BA03:6745:EF1C:683D
The increased bit count and the availability of 32 hexadecimal characters results in a significantly larger address space as compared to IPv4. IPv4 theoretically offers a maximum of 4,294,967,296 unique addresses, but certain address ranges are not allowed to be used for public addressing (such as 127.x.x.x, 10.x.x.x, 172.16.x.x, 192.168.x.x, etc.). So the real quantity of publicly available IPv4 addresses is considerably less than absolute limit of 4,294,967,296. IPv6, in contrast, offers the potential for such a large quantity of addresses that it is difficult to grasp. This number is 3.4×1038, resulting in a grand total of 340,282,366,920,938,463,463,374,607,431,768,211,456 possible addresses. This quantity is so huge that every star in the universe could have 340,282,366,920,938 universally unique IP addresses (the latest estimates are that there are 1022 to 1024 stars in existence). This means that each star would have a unique address space that is at least 80,000 thousand times greater than our current IPv4-based global Internet.
If you have experience with IPv4 subnetting, you are probably in the habit of being frugal with your address consumption. With IPv6, you can have so many subnets and hosts on each subnet that you no longer need to pinch IP addresses. IT professionals will need to make an effort to abandon the fear of using “too many IP addresses”. Believe it or not, you can simultaneously be wasteful with address space and have room to support future network growth. However, you will still need to follow sound IP addressing practices; i.e., do not simply toss IPv6 addresses around in a haphazard manner. Allocate them in logical, consistent, and meaningful ways (i.e., use patterns) and be sure to use an inventory tool to keep orderly records of address assignments (see IP Address Management tools on Wikipedia) as you are not likely to memorize IPv6 addresses. DNS will be even more of your friend than with IPv4.
The IPv4 addressing scheme includes network, subnet, and host divisions. IPv6, however, provides hierarchical addressing based on prefixes rather than the address classes of traditional IPv4. IPv6 addresses adhere to this format:
Global routing prefix | Subnet ID | Interface ID |
|---|---|---|
| x bits | y bits | 128 – (x+y) bits |
The global routing prefix is a hierarchically structured value assigned to a site. The subnet ID is an identifier of a link within the site. The interface ID is a unique identifier for a networked device on a given link (of course, multihomed devices have more than one interface).
As with IPv4 and its dotted decimal notation, it is important to understand IPv6 addresses not as they are commonly depicted (with hexadecimal characters) but as collections of bits. Here is IPv6 address 2001:DB8::2F3B:2AA:FF:FE28:9C5A in its “true” binary form:
0010000000000001 0000110110111000 0000000000000000 0010111100111011 0000001010101010 0000000011111111 1111111000101000 1001110001011010As in IPv4, some of the bits in an IPv6 address stand for the network/subnet and the other bits stand for the host/interface. IPv6 does not use subnet masks (such as 255.255.192.0) but rather network prefixes to delineate the network/host boundary. Prefixes are all addresses that start with the same series of bits, and they are written in slash notation (such as /48). In other words, the prefix specifies how many of the leftmost contiguous bits of the address comprise the network. For example, the host address 29D0:14C7:4B92:9BD29:1A2B:E5F6:8C4D:1025/64 shows that the network prefix is the first 64 bits of the address (highlighted in bold). In other words, the network this host belongs to is 29D0:14C7:4B92:9BD29:0000:0000:0000:0000/64.
As another example, this is a 60-bit prefix (underlined): 14DE:0000:0000:BE50:0000:0000:0000:0000/60 (each hex digit is worth 4 bits, and fifteen digits are underlined). This prefix, 2001:0CD9::/32, contains all the interface addresses from 2001:0CD9:0000:0000:0000:0000:0000:0000 to 2001:0CD9:FFFF:FFFF:FFFF:FFFF:FFFF:FFFF. Similarly, prefix 2001:0CD9:1B3D::/48 contains all interface addresses from 2001:0CD9:1B3D:0000:0000:0000:0000:0000 to 2001:0CD9:1B3D:FFFF:FFFF:FFFF:FFFF:FFFF.
The first address in the paragraph above, 14DE:0000:0000:BE50:0000:0000:0000:0000/60, could be condensed to 14DE:0:0:BE50::/60. Unlike IPv4, addresses in IPv6 can be abbreviated to make them simpler to read and write. If an IPv6 address block (remember each address has 8 blocks) is comprised solely of 0s (zeroes), then it can be compressed into just one zero. In other words, address FE38:0000:124C:C1A2:BA03:6745:EF1C:683D could be written as FE38:0:124C:C1A2:BA03:6745:EF1C:683D. If there happen to be contiguous blocks of only 0s in an address, then these blocks can be omitted altogether. For example, FE38:0:0:0:BA03:6745:EF1C:683D could be represented as FE38::BA03:6745:EF1C:683D. This two-colon abbreviation may only be applied once in an address. Therefore, address FE00:0000:0000:0004:0000:0000:0000:0047 could be rewritten as FE00::4:0:0:0:47 or FE00:0:0:4::47, but not as FE00::4::47.

Image source: Wikimedia Commons
Network addressing can now be done on half-byte (nibble) boundaries (remember, a byte is eight bits, and each hex character in an IPv6 address represents four bits). What this means is that prefix boundaries can occur within the binary value of a single hex character. Each character is four bits, so if the prefix length is not a multiple of four, the binary separation will take place within a hexadecimal character.Organizations requesting IPv6 address allocations from their local regional Internet registry (RIR) are given address ranges with /48 prefixes. This means that the first three blocks (total of 48 bits) are fixed and do not change. Typically, organizations with a /48 range will then use the fourth block for the creation of subnets. So initially a /48 prefix is assigned, such as 2001:DB8:4B92::/48. Then the fourth block is populated to create subnets: 2001:DB8:4B92:xxxx::/64, where xxxx stands for hexadecimal digits 0000-FFFF. You should get used to seeing the /64 prefix length. Standard IPv6 addressing (specified in RFC 4291) requires that most unicast addresses use a 64-bit interface identifier. Additionally, this is a requirement of Stateless Address Auto Configuration (RFC 4862) and any network expecting SLAAC to occur must have a /64 prefix available.
A /64 prefix can provide for 18,446,744,073,709,551,616 addresses.
↑ Up to page menu
IPv6 address types
IPv6 addresses can fall into three categories: unicast, multicast, and anycast. These also exist in IPv4. However, notice that IPv6 does not utilize broadcast addresses.A unicast address is an identifier for a single interface. In other words, the final destination for packets sent to a unicast address is only to interface identified by that address.
A multicast address is an identifier for a group of interfaces. The intended final destination for packets sent to a multicast address is all the interfaces identified by that address. An interface may belong to several multicast address groups. Multicast addresses cannot function as source addresses, only destinations. The multicast entry on Wikipedia lists several instances in which hosts would transmit multicast rather than unicast data streams.
Like multicasts, an anycast address is an identifier for a group of interfaces. However, packets sent to anycast addresses are not delivered to all interfaces in that group. Instead, packets sent to an anycast address get delivered to the closest member of a group, according to the metric utilized by the routing protocol. In this way, anycasts are sort of like a hybrid between unicast and multicast addresses. The important point to remember is that packets sent to an anycast address will be delivered to one (and only one) of the nodes that are listening on that anycast address.
↑ Up to page menu
IPv6 unicast address types
In IPv6 there are several types of unicast addresses, such as global unicast, unique local unicast, and link-local unicast.Global unicast addresses. These addresses can be regarded as the IPv6 equivalents of public IPv4 addresses. Global unicast addresses are publicly routable, globally unique, and the prefix 2000::/3 is designated for them (all addresses that begin with hexadecimal 2 or 3).
Link-local addresses. Used by autoconfiguration protocols like Neighbor Discovery Protocol (NDP), link-local addresses are automatically configured by IPv6 interfaces. Link-local addresses are used to communicate over a single physical or logical subnet, such as a typical Ethernet-based LAN. In this way, link-local addresses are similar to IPv4′s APIPA address range. APIPA is a feature of Microsoft Windows that acts as a DHCP failover mechanism (when a DHCP request or server fails, APIPA automatically allocates addresses in the private range 169.254.0.1 to 169.254.255.254).
The link-local default prefix is FE80::/10. Routers will not forward any packets to other links if the source or destination addresses are link-local.
Unique local addresses. Unique local addresses (ULAs) have replaced the deprecated site-local addresses which were previously standard in IPv6. Routers would not forward any packets to other sites if the source or destination addresses were site-local. ULAs are similar in that they are usually only routed within one site, but they can also be routed among a set of sites. However they are not to be routed globally (i.e., on the Internet) even though they are globally unique. Therefore you could join two subnets and not have to worry about IP address collisions.The standard ULA prefix is FC00::/7. Unique local addresses are similar to IPv4′s private (RFC 1918) address ranges.
The loopback address in IPv6 is 0:0:0:0:0:0:0:1/128, or ::1/128. As you recall, the IPv4 loopback address is 127.0.0.1/8. In both IPv6 and IPv4, the loopback address serves the same purposes. For instance, if you ping the loopback address and you receive replies, it’s a sign that TCP/IP protocol suite is properly functioning on the local host. To do this in IPv6, the command is
ping6 ::1.The unspecified address, 0:0:0:0:0:0:0:0/128 or ::/128, indicates the absence of an address and therefore cannot be assigned to any interface or used as a destination address. Instead it serves as the source address of any packets sent by an initializing host before it has learned its own proper IPv6 address. Ipv6 routers will not forward requests with the unspecified address as the source.
The loopback and unspecified addresses are established in RFC 4291.
IPv4-mapped IPv6 address. These unicast addresses are used by applications that transmit in IPv6 to allow them to talk with IPv4 hosts. The first 80 bits are zero, the next sixteen bits are 1, and the remaining 32 bits are the IPv4 address in dotted decimal notation. For example, ::FFFF:192.0.10.25 represents the IPv4 address 192.0.10.25. Standardized in RFC 4038.
IPv4-compatible IPv6 address. The IPv4-compatible address, 0:0:0:0:0:0:a.b.c.d (where a.b.c.d is the dotted decimal representation of an IPv4 address), is used by dual stack hosts to communicate using IPv6. When the IPv4-compatible address is used as an IPv6 destination, the IPv6 traffic is automatically encapsulated with an IPv4 header and sent to the destination using an IPv4 pathway. Example address: ::192.168.10.25. Deprecated since RFC 4291.
↑ Up to page menu
IPv6 multicast address types
Multicasts can be easily identified as they have a prefix of FF (or 11111111 in binary). The multicast ‘all nodes on link’ address of FF02::1 is as close to a traditional broadcast address as IPv6 gets.The following scopes apply to multicast addresses: interface-local (a single interface only), link-local (used by hosts when communicating with neighboring nodes on the same link), subnet-local (for subnets that span multiple links), admin-local (must be administratively configured), site-local (the site or organization network, not to be forwarded outside of scope), organization-local (intended to span multiple sites belonging to one organization), and global (globally unique, i.e. across the Internet).
Additionally there are a few defined types of multicast groups.
‘All nodes’ multicast groups
These groups identify all IPv6 nodes within a given scope.
- Interface-local, all nodes (FF01::1)
- Link-local, all nodes (FF02::1)
These groups identify all IPv6 routers within a given scope.
- Interface-local, all routers (FF01::2)
- Link-local, all routers (FF02::2)
- Site-local, all routers (FF05::2)
Solicited-node multicast addresses are used by Neighbor Discovery Protocol for obtaining the Layer 2 addresses of other nodes (similar to ARP).
IPv6 reserved prefixes
The following IPv6 prefixes are reserved for certain purposes:- ::/96: The zero prefix denotes addresses that are compatible with the previously used IPv4 protocol.
- ::/128: the unspecified address (all zeroes).
- ::1/128: the loop back address.
- 64:FF9B::/96: NAT64 well-known prefix.
- 2000::/3: Global unicast.
- 2001::/32: Teredo prefix.
- 2001:DB8::/32: For use as IPv6 examples (in tutorials, trainings, essays, etc.). 2001:0DB8: should be rendered as 2001:DB8: to encourage the habit of suppressing leading zeroes.
- 2002::/16: 6to4 prefix.
- FC00::/7, FD00::/8: Unique Local Address (ULA) prefixes. Routed only within a predefined set of cooperating sites.
- FEC0::/10: This is a site-local prefix (deprecated by the IETF).
- FF00::/8: Generic prefix for multicast addresses.
- FF01::1: Interface-local, all nodes (multicast).
- FF01::2: Interface-local, all routers (multicast).
- FF02::1: Link-local, all nodes (multicast).
- FF02::2: Link-local, all routers (multicast).
- FF02::5: OSPF messages (multicast).
- FF02::6: OSPF messages (multicast).
- FF02::8: IS-IS messages (multicast).
- FF02::9: RIPv2 messages (multicast).
- FF02::A: EIGRP messages (multicast).
- FF02::D: PIM messages (multicast).
- FF02::16: MLDv2 reports (multicast).
- FF02::1:2: DHCP relay agents on local segment (multicast).
- FF02::1:FF00:0/104: Solicited-node address (multicast).
- FF02::1:3: All LLMNR hosts on local segment (multicast).
- FF02::2:FF00:0/104: Node Information Queries (multicast).
- FF05::1:3: Site-local, all DHCP servers (multicast).
- FF05::1:4: Site-local, all DHCP relays (multicast).
- FF05::2: Site-local, all routers (multicast).
- FF0x::C: Simple Service Discovery Protocol (multicast).
- FF0x::FB: Multicast DNS (multicast).
- FF0x::101: Network Time Protocol (multicast).
- FF0x::108: Network Information Service (multicast).
- FF0x::114: Used for experiments (multicast).
- FE80::/10: the link-local prefix (signifies that the address is valid only on the local physical link).
IPv6 automatic address acquisition by hosts
IPv6 hosts can utilize stateless autoconfiguration of IP address parameters. Stateless address autoconfigration (SLAAC) uses local host information along with information advertised by routers (no DHCP server is required). This process (described in RFC 4862) involves using the host’s MAC address to generate an EUI-64 address and then joining it to the 64-bit local link prefix (FE80::/64) which is learned from a router. In this sense, local routers kind of act like DHCP servers because they send out “router advertisements” (RAs) that contain the first 64 bits of an IPv6 address (the local link prefix). To generate EUI-64 addresses from their MAC addresses, the hexadecimal values of 0xFF and 0xFE are inserted between the third and fourth bytes of the MAC address. To then create an IPv6 interface identifier from the EUI-64 address, the Universal/Local bit (the second low-order bit of the first byte of the EUI-64 address) is turned to 0 if it is a 1, or turned to 1 if it is a 0). For example, for the EUI-64 address of 00-60-09-FF-FC-53-F7-D6, the second low-order bit of 0×00 is 0, which, when complemented, becomes a 1. The result is that for the first byte, 0×00 becomes 0×02. Therefore, the IPv6 interface identifier corresponding to the EUI-64 address of 00-60-09-FF-FC-53-F7-D6 is 02-60-09-FF-FC-53-F7-D6. This process is explained in RFC 4291.To avoid the possibility of SLAAC generating a duplicate link-local address, Duplicate Address Detection (DAD) is then invoked. This combination of IPv6 addresses generated from interface MAC addresses plus DAD means that collisions of link-local addresses are virtually no longer a concern. This news will come as a relief for any network administrators who have ever had to merge two or more subnets that used addressing schemes in, for example, the 192.168.x.x or 10.x.x.x ranges.
Like DHCP in IPv4, IPv6 hosts can also be configured to acquire connectivity parameters from DHCPv6 servers. IPv4 clients use DHCP broadcasts to locate DHCP servers, and since broadcasts are extinct in IPv6, clients use specialized multicasts to locate DHCPv6 servers. These multicasts use the reserved address FF02::1:2. One notable difference between DHCP and DHCPv6 is that while DHCP can inform clients which node to use as the default gateway, DHCPv6 does not do this. The default gateway should be a link-local router that can reliably make its own existence known via router advertisements. So IPv6 clients must be informed of the default gateway address via the SLAAC process. Another difference between DHCP and DHCPv6 is that while DHCP is a very “tried and true” service, DHCPv6 did not perform very well in a 2011 vendor-neutral interoperability test.
↑ Up to page menu
IPv6 and security
Unlike IPv4, IPv6 was designed with security in mind. Take ICMPv6 for example. ICMPv6 is more important for proper IPv6 functionality than traditional ICMP is for IPv4. Specifically, ICMPv6 is responsible for providing diagnostic functions and reporting errors if packets are not successfully delivered. It also enables Neighbor Discovered and Multicast Listener Discovery (MLD). However, many firewalls block ICMP as a measure to protect against ping sweeps and ping-related denial of service attacks such as such as the Ping of Death, Smurf attack, and ping floods. ICMPv6 will most likely get the same treatment on many IPv6-capable perimeter devices. In response, ICMPv6 was designed to be compatible with IPSec to enable authentication and encryption. In fact, IPv6 is required by its designers to natively support IPSec. Another example is the integration of DHCPv6 and network access policies. Before DHCPv6 servers reply to client requests, they can check network access control policies to ensure that only valid hosts receive the IP parameters which they are requesting. A final example deals with network scanning, a step often taken by hackers looking to enumerate network hosts and find weak targets. Because of the aforementioned vastness of the IPv6 address space, network scanning is more difficult. Randomly scanning for vulnerable hosts is impractical at best, probably impossible.However, like all new technologies, IPv6 will not be free of vulnerabilities. There will definitely be bugs found in its underlying code, and as the protocol becomes more and more diffused throughout global networks, security holes will surely be discovered. Indeed, although IPv6 is just at the dawn of its eventual worldwide deployment, there has already been a considerable quantity of IPv6 vulnerabilities discovered in recent years. Websites that track computing vulnerabilities have catalogued numerous IPv6 holes and exploits, and many more protocol weaknesses will be uncovered in coming years. For listings of the vulnerabilities published so far, you can visit:
- Open Source Vulnerability Database’s IPv6 vulnerabilities
- CERT Vulnerability Notes Database (search for ‘IPv6′)
- Mitre’s CVE List IPv6 vulnerabilities
- NIST’s National Vulnerability Database IPv6 vulnerabilities
IPv6 should definitely not be regarded as a miraculous cure-all that will immediately reduce network vulnerabilities and threat vectors. The same basic threats and respective security measures and guidelines apply to both IPv4 and IPv6. For example, even though IPv6 is better suited to resist scanning of address blocks as previously mentioned, targeted scanning scanning and probing against specific hosts is still very much possible. Packet sniffing is also still a valid threat. Such security concerns should serve to motivate organizations to to transition to IPv6 sooner rather than later because a hastily deployed IPv6 network is one which will not be as locked down as its IPv4 counterpart or predecessor. Therefore it’s advisable to upgrade to IPv6 when there is plenty of time to spare for testing and gradual deployment.
Most networks today already have many IPv6-enabled hosts, including every node running Windows Vista, Windows 7, Mac OS/X, and all modern Linux, Unix, and BSD. These hosts can use SLAAC as previously described to communicate with other IPv6 network devices and services on the same LAN, and if they can contact an IPv6-enabled router then there may be unapproved, “rogue” IPv6 traffic on your network which could evade IPv4-based security measures. Even though the built-in Windows Firewall is compatible with IPv6, Windows hosts have the potential to be particularly worrisome because they do not support two IETF security standards:
SEcure Neighbor Discovery (SEND) (described in RFC 3971) can provide protection for Router Solicitation and Router Advertisement messages. SEND can also be used to provide protection for Neighbor Solicitation and Neighbor Advertisement message exchanges for address resolution or neighbor unreachability detection, providing protection against Neighbor Discovery-based denial of service (DoS) attacks by nodes with statically configured IPv6 addresses. In contrast, there is no mitigation against Address Resolution Protocol (ARP) DoS attacks for IPv4. However, Microsoft does not support SEND in any version of Windows…RFC 3118 defines a method to provide authentication for DHCP message exchanges for IPv6 or IPv4 DHCP-based configuration. Windows XP and Windows Server 2003 do not support DHCPv6-based IPv6 address configuration. Microsoft supports DHCPv6 in Windows 7, Windows Server 2008 R2, Windows Vista, and Windows Server 2008. However, Microsoft does not support RFC 3118.Windows 7 and 8 are also vulnerable to a denial of service attack which can be triggered by rogue IPv6 router advertisements.
An attack tool targeting IPv6, THC-IPv6, is available for download for use by hackers and ethical hackers alike. There are, however, a few programs that can help secure your IPv6 hosts. One is NDPMon, which can detect suspicious ICMPv6 traffic. Another is 6Guard, which is specifically designed to counter THC-IPv6.
Now that Nmap is compatible with IPv6, there are a handful of Nmap scripts that can be used to assess IPv6 hosts.
↑ Up to page menu
IPv6 and traditional NAT
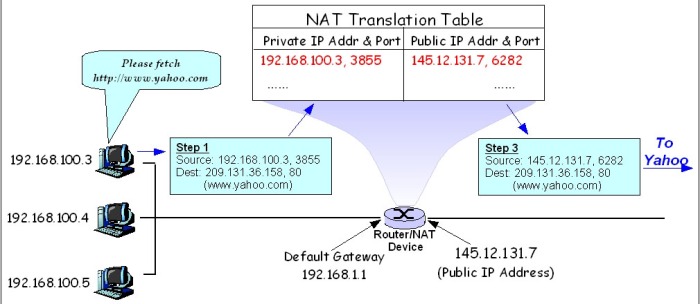
The potential extinction of NAT in IPv6 networks is one of the most controversial changes from IPv4. NAT devices replace the private (RFC 1918) source addresses in outbound packets with public IP addresses. By keeping track of which internal host sent which packets, NAT devices can allow many hosts to share one public IP address. Conventional IPv6 wisdom claims that since there is such a ridiculously large number of addresses to go around, it is no longer necessary to conserve public address space and “hide” your internal hosts behind NAT devices.
Traditional IPv4 Network Address Translation (NAT) operation
Image source: Wikibooks
Many system administrators take issue with the recommendation to retire NAT because even if public IP address availability is no longer a concern, they still do not want their private network topology exposed by providing each of their hosts a publicly discoverable IPv6 address. Therefore they are reluctant to abandon NAT as it shields their private networks from prying eyes on the Internet. As such, NAT has been an important tier in the “defense in depth” information security strategy (a best practice security model). However, NAT also represents a single point of failure in network communications and is a convenient target for denial of service attacks. Furthermore, the obscurity which NAT offers its “hidden” internal hosts should not be confused with a true security measure.Functionally speaking, NAT can be seen as a sort of “hack” solution for networks because all ingress and egress packets are examined and altered, thereby introducing extra complexity and hence, more potential for erroneous configurations and bugs. Wikipedia’s entries on NAT and NAT traversal explain NAT’s disadvantages and drawbacks in more detail. As Iljitsch van Beijnum states on ArsTechnica:
Architecturally, NAT is a bad thing. It breaks all kinds of assumptions built into protocols, so it can get in the way of applications. This is especially true for peer-to-peer applications such as BitTorrent, but also VoIP (including Skype). However, over the years application builders have figured out ways to work around NAT. One method involves talking to the local home gateway that’s performing NAT, and asking it to forward incoming connections using a port mapping protocol. This works very well when you run a NAT in your own home, but not so much when your ISP runs a big NAT. Not only will different users compete for the best port numbers, but also the commonly used port mapping protocols (UPnP, IGD and NAT-PMP) can’t talk to a NAT several hops away.Nevertheless, an experimental RFC does exist describing the function of traditional NAT in IPv6 (RFC 6296). The Internet Architecture Board (IAB) makes their feelings about NAT in IPv6 known in RFC 5902.
Making peer-to-peer applications work may or may not be a high priority for ISPs, who also tend to be in the video content distribution and/or voice calling business. Worse, ISP-provided NAT may actually break IPv6 tunneling mechanisms that allow people to gain IPv6 connectivity if their ISP doesn’t provide it. And deploying these expensive and complex new NAT boxes may take away resources that could otherwise be used to deploy IPv6 in the network.
↑ Up to page menu
IPv4-to-IPv6 transition methods
For obvious reasons, the switch to IPv6 cannot be made abruptly with little or no preparation. IPv4 has proven to be a very resilient protocol and is entrenched in modern networks. Regardless, the IETF has specified in RFC 6540 (April 2012) that going forward all IP-capable devices are to be compatible with IPv6, not just IPv4. The evolution to IPv6 will be gradual and both protocols will exist side-by-side for quite some time. However, you should begin planning to make your public servers (DNS, email, Web) reachable via IPv6. Make it a priority to ensure that your public websites and Internet-facing applications can answer IPv6 requests. As IPv6 becomes more prevalent, standard business considerations will kick in if your sites and services start to lose customers and hits, and then you will face the challenge of enabling IPv6 support in a hurried, stressful manner. The law of supply and demand will also rear its head when the final few IPv4 addresses are available – they will surely be expensive.When you decide to enable and support IPv6, many standard network security considerations will apply. For instance, the IPv4-based access control lists (ACLs) on your network perimeter must be coupled with new IPv6 ACLs that offer the same level of protection. On the client side, most operating systems released in the 21st century are equipped to handle IPv6. If a modern version of Linux or Windows boots up and detects an IPv6 router on the LAN that advertises an IPv6 prefix, it will generate an IPv6 address. This functionality will surely prove beneficial during IPv4-to-IPv6 network upgrades because many hosts will remain online and users will be able to continue working. However, this also means that there could be unapproved, covert IPv6 traffic traversing your network.
Many respected and influential enterprises have already made the decision to embrace IPv6. Google, for instance, has already acquired a tremendous amount of IPv6 addresses. Google owns every address with the prefix 2001:4860::/32. Google has also deployed public IPv6 DNS servers (2001:4860:4860::8888 and 2001:4860:4860::8844). Other major industry giants such as Microsoft, Cisco, Juniper, Red Hat, Verizon, Sprint, AT&T, Comcast, Netgear, D-Link, and Belkin have also rallied to the call to roll out IPv6 services.
Complicating the deployment of IPv6 is the fact that (quite regrettably) IPv4 and IPv6 are not directly compatible. In other words, hosts connecting solely over IPv4 cannot directly communicate with hosts connected solely via IPv6. In response to this challenge, several interprotocol transition solutions have been developed. These transition technologies are mechanisms designed to enable service providers and network operators to migrate their subscriber base (users) from IPv4 to IPv6. In the ideal interim transition environment, both IPv4 and IPv6 are fully deployed across all the infrastructure, meaning that all networked hosts (such as servers, workstations, mobile devices, etc.) and all networking devices (such as routers, switches, firewalls, etc.) can process both IPv4 and IPv6. Additionally all content, applications, and services are available via both protocols. To end users, however, the utilization of two different protocols should remain transparent. In the ideal end state environment, IPv6 has fully replaced IPv4 and all nodes communicate solely via IPv6.
One undesirable side effect of these transition methods is that they may end up actually delaying the transition from IPv4 to IPv6. Remember, the idea is to get weaned off IPv4, not to artificially prolong its lifespan. It is quite unfortunate that IPv6 is almost twenty years old but has yet to achieve widespread adoption, particularly in the USA. One very positive outcome of rolling out IPv6 is that such a protocol upgrade is a one-time deal…you and/or your successors will never have to worry about undergoing a similar process for a long, long time. If the estimated lifespan of IPv4 ends up being about fifty years (it was standardized in 1981), then it’s very likely that IPv6 will exist as a viable networking protocol for hundreds of years after we are gone.
The three main types of transition mechanisms are:
- Dual stack
- Translation
- Tunneling (packet encapsulation)
Dual stack
In a dual stack environment, IPv4 and IPv6 can both traverse all segments of the network. Dual stack means that key network nodes can run both IPv4 and IPv6 simultaneously, so they can communicate with IPv4 hosts using IPv4 and with IPv6 hosts using IPv6. When a connection needs to be established with an IPv4-only host, the IPv4 path is used. When a connection needs to be established with an IPv6-only host, the IPv6 path is used. When the destination host can understand either protocol, IPv6 should be the preferred protocol. If the attempt at IPv6 fails, then IPv4 will be used instead. Dual stack hosts query DNS servers for both A records and AAAA records (AAAA should be preferred).Translation
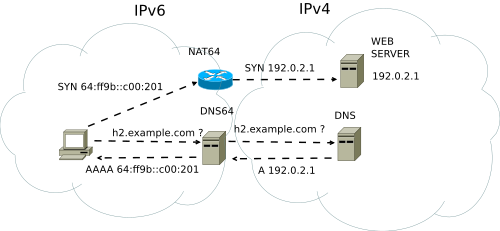
NAT64 and NAT46 are translation methods (NAT-PT has been deprecated by the IETF). NAT64 is necessary when IPv6-only hosts needs to communicate with IPv4-ony hosts. NAT46 is necessary when IPv4-only hosts need to communicate with IPv6-only hosts. Instead of tunneling one protocol inside the other, NAT translation actually converts IPv4 addressing to IPv6 and vice versa. This technique is similar to how NAT devices translate private ranges of IPv4 addresses (specified in RFC 1918) into public range IPv4 addresses. A special prefix,64:ff9b::/96, is used to map IPv4 addresses to IPv6 addresses. A modification to DNS, DNS64, is also needed. DNS64 synthesizes an AAAA record even when no IPv6 address is found for the destination host (i.e., when DNS only replies with traditional A records).Typically NAT is performed by customer premises equipment (CPE) such as your home or business router. When service providers deploy NAT gear for IPv6-IPv4 translation, this practice is known as Large Scale NAT (LSN) or Carrier-Grade NAT (CGN).
NAT64 and NAT46 are described in more detail by this IETF draft. The NAT64 protocol specification can be found in RFC 6146. IPv6/IPv4 translation as a whole is discussed in RFC 6144.

NAT64
Image source: Wikimedia Commons
Tunneling
Tunneling involves encapsulating IPv6 packets inside IPv4 packets or vice versa. When IPv6 packets must cross a section of the network that only supports legacy IPv4, the IPv6 packets are put inside IPv4 packets, transmitted across the IPv4-only part of the network. Then the IPv4 packaging is stripped and the packets continue to their IPv6-addressed destinations. Tunnels can be manually configured (static) or dynamically generated. RFC 4213, ‘Basic Transition Mechanisms for IPv6 Hosts and Routers’, defines four generic types of tunneling mechanisms:Router-to-Router. IPv6/IPv4 routers interconnected by an IPv4 infrastructure can tunnel IPv6 packets between themselves. In this case, the tunnel spans one segment of the end-to-end path that the IPv6 packet takes.Some popular tunneling techniques include:
Host-to-Router. IPv6/IPv4 hosts can tunnel IPv6 packets to an intermediary IPv6/IPv4 router that is reachable via an IPv4 infrastructure. This type of tunnel spans the first segment of the packet’s end-to-end path.
Host-to-Host. IPv6/IPv4 hosts that are interconnected by an IPv4 infrastructure can tunnel IPv6 packets between themselves. In this case, the tunnel spans the entire end-to-end path that the packet takes.
Router-to-Host. IPv6/IPv4 routers can tunnel IPv6 packets to their final destination IPv6/IPv4 host. This tunnel spans only the last segment of the end-to-end path.
6to4
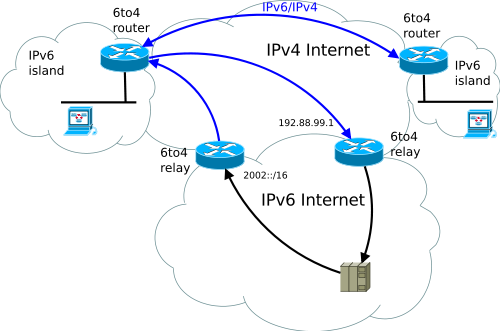
6to4, Teredo, and ISATAP are automatic tunneling techniques. 6to4 uses a default relay tunnel address, 192.88.99.x and a default gateway of 192.88.99.1. Any traffic directed to this IPv4 address range is probably carrying encapsulated 6to4 IPv6 traffic (6to4 packets start with 2002::/16). 6to4 works well when a 6to4 router exists at the edge of the site. The 6to4 router uses a public IPv4 address to construct the 6to4 prefix and encapsulates and decapsulates IPv6 traffic sent to and from nodes in the site. So, 6to4 needs configuration of a public IPv4 address and the implementation of 6to4 routing functionality on the site’s edge device. Many small office/home office (SOHO) configurations use an IPv4 NAT device for Internet connectivity. In most NAT configurations, the device providing NAT functionality is not capable of acting as a 6to4 router. Even if 6to4 were universally supported in Internet edge devices, there are some Internet connectivity configurations that contain multiple levels of NATs.

6to4
Image source: Wikimedia Commons
TeredoTeredo solves the issues of the lack of 6to4 functionality in modern-day Internet edge devices and multilayered NAT configurations by tunneling IPv6 packets between the hosts within the sites. In contrast, 6to4 tunnels IPv6 packets between the edge devices. Teredo allows IPv6 connectivity between IPv6 and IPv4 nodes that are separated by one or more NAT devices. Teredo traffic is composed of IPv6 packets that have been encapsulated as IPv4-based UDP messages, and UDP can be translated universally by NAT devices and can traverse multiple NAT layers. Teredo functionality is explained more thoroughly in Technet’s Teredo overview (Teredo was developed by Microsoft). Teredo is also described in RFC 4380.
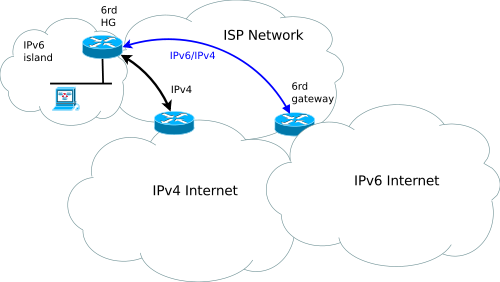
6rd
6RD has a lot in common with 6to4. 6to4 works by relaying traffic between native IPv6 and IPv4 using relay servers which advertise common IPv4 and IPv6 prefixes to networks they are prepared to provide relay services for, but there is no guarantee that all native IPv6 hosts have a working route toward such a relay. With 6rd, this model is changed by making each ISP use one of its own IPv6 prefixes instead of the special 2002::/16 prefix standardized for 6to4. The 6rd protocol specification can be found in RFC 5969.

6rd
Image source: Wikimedia Commons
6in46in4 is the encapsulation of IPv6 packets in IPv4 packets. In 6in4, the IPv4 packet header is immediately followed by the IPv6 packet. This means that the encapsulation overhead is simply the size of the IPv4 header (20 bytes) which avoids MTU packet fragmentation. More details can be found in RFC 4213.
6over4
6over4 is a transition mechanism which allows isolated IPv6 hosts, located on a physical link which has no directly connected IPv6 router, to use an IPv4 multicast domain as their virtual local link. A 6over4 host uses an IPv4 address for the interface in the creation of the IPv6 interface ID, placing the 32-bit IPv4 address in the low order bits and padding to the left with 0′s for a total of 64 bits. The IPv6 prefix used is the normal IPv6 prefix, and can be manually configured or dynamically learned by way of SLAAC.
6over4 is officially documented in RFC 2529. Semantic differences between the terms “6in4″ and “6over4″ are addressed in a 2005 IETF draft document.
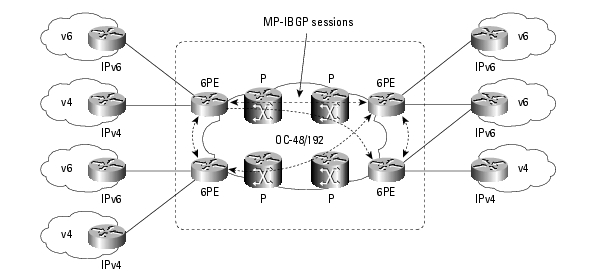
6PE
Cisco’s IPv6 Provider Edge (6PE) is a tunneling solution for MPLS backbones.

6PE
Image source: Cisco Systems
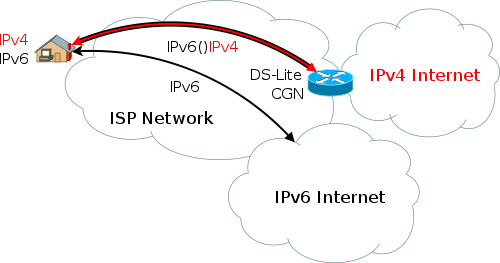
DS-LiteDual Stack Lite (DS-Lite) uses 4in6 tunnels to send traffic to a DS-Lite server which then NATs the traffic though a tunnel. This allows for IPv6-only connections between the customer site and the service provider’s Large Scale NAT (LSN), but instead of translating from IPv4 to IPv6 as in NAT464, the IPv4 packets are tunneled to the LSN, so no translation needs to be performed. More info on DS-Lite can be found here and here. Standard specification is in RFC 6333.

DS-Lite
Image source: Wikimedia Commons
DSTMDual Stack Transition Mechanism (DSTM) encapsulates IPv4 packets within IPv6 (4in6). Standard specification can be found on IETF.org. DSTM is designed to rapidly reduce the reliance on IPv4 routing and is intended for IPv6-only networks in which hosts still occasionally need to communicate directly with other IPv4 hosts.
ISATAP
Intra-site Automatic Tunnel Addressing Protocol (ISATAP). Unlike 6to4 tunnels, ISATAP tunnels do not work if IPv4 NAT is used between the tunnel endpoints. The IETF describes ISATAP in RFC 5214.

ISATAP
Image source: Microsoft
↑ Up to page menuConfiguring IPv6 on Linux
The Linux kernel has provided IPv6 support since as far back as 1996 (since kernel v2.4). Not surprisingly, configuring IPv6 in Linux involves editing text files using vi or a text editor such as gedit.In the Red Hat Linux family (which includes Fedora and CentOS), open up the
/etc/sysconfig/network file and add/edit these lines:NETWORKING_IPV6=yes
IPV6FORWARDING=no
IPV6_AUTOCONF=no
IPV6_AUTOTUNNEL=no
IPV6_DEFAULTGW=FE80::1
IPV6_DEFAULTDEV=eth0The second step is to open
/etc/sysconfig/network-scripts/ifcfg-eth0 (assuming eth0 is the adapter in question) and add/edit these lines:IPV6INIT=yesIPV6ADDR=2001:DB8:xxxx:yyyy::zzzz/64 (this line to configure a static IPv6 address)Now enter the command:
service network restartFor Debian-based Linuxes (including Ubuntu and Mint), open
/etc/sysctl.conf and add/edit this line:net.ipv6.conf.eth0.accept_ra=0Then open
/etc/network/interfaces and add/edit these lines:iface lo0 inet6 loopback
iface eth0 inet6 static
address 2001:DB8:xxxx:yyyy::zzzz (your static IPv6 address, if needed)netmask 64
gateway FE80::1Now enter the command:
sudo /etc/init.d/networking restartIPv6 traffic blocking and filtration in Linux is possible with the ip6tables firewall. On your firewall host, issue the command
ip6tables -P INPUT DROP to block all non-permitted traffic. Then enable inbound traffic as you see fit; for example, to permit HTTP (port 80) to reach your web server, enter ip6tables -A INPUT -d 2001:db8::1234:abcd:90ab:5678 -p tcp --dport 80 -j ACCEPT. Ip6tables uses the same command syntax as iptables.If you want to configure a Linux host to act as an IPv6-capable router, you must enable the Router Advertisement Daemon (RADVD). RADVD listens for Router Solicitations (RS) and responds with Router Advertisement (RA) replies. This is the same process as described in the IP address acquisition section above. You can tweak RADVD’s parameters in
/etc/radvd.conf.Linux clients can utilize Teredo tunneling courtesy of the Miredo tunneling client.
Be sure to have a look at the ‘IPv6 and Linux’ links below.
↑ Up to page menu
Configuring IPv6 on Windows
Windows Server 2008 was the first version of Windows to ship with IPv6 enabled by default (Microsoft’s calls its implementation of IPv6 in Server 2008 and Windows Vista the “Next Generation TCP/IP Stack”). Windows 8 not only ships with IPv6 enabled by default, it is actually the operating system’s preferred protocol over IPv4. Windows Vista, 7, Server 2008, and 8 will enable Teredo and 6to4 by default. What this means is that the 6to4 tunneling protocol is enabled in Windows 7, Windows Vista, Windows Server 2008 R2, and Windows Server 2008 when an interface is assigned a public IPv4 address (i.e., an address not in the private ranges of 10.0.0.0/8, 172.16.0.0/12, or 192.168.0.0/16). 6to4 will automatically assign an IPv6 address to the 6to4 tunneling interface for each such address that is assigned, and 6to4 will dynamically register these IPv6 addresses on the assigned DNS server. To disable IPv6 or enable/disable certain IPv6-related features, follow the instructions in Microsoft KB929852.With a little effort, IPv6 can be installed and enabled on Windows XP and Windows Server 2003. To install IPv6 on Windows XP, open up a command prompt and type:
netsh int ipv6 install. To uninstall, type: netsh int ipv6 uninstall. If you prefer to install/uninstall with the Windows XP graphical user interface (GUI), see instructions here. However, XP and Server 2003 are not compatible with DHCPv6 (though they can engage in SLAAC). Also note that while Windows XP can only perform DNS queries over IPv4, it can query for AAAA records.Instructions to install, configure, and uninstall IPv6 on Windows Server 2003 can be found here and here.
In Windows XP and Windows Server 2003, the IPv6 interface ID is derived from the Extended Unique Identifier (EUI)-64 address. In Windows Vista and Windows Server 2008, the interface ID by default is randomly derived, rather than based on the EUI-64 address. You can disable random interface IDs with the
netsh interface ipv6 set global randomizeidentifiers=disabled command.IPv6 in Windows XP and Windows Server 2003 uses the Automatic Tunneling Pseudo-Interface for encapsulating IPv6 packets with an IPv4 header so that they can be transmitted across an IPv4 network. By default, IPv6 configures a link-local Intra-Site Automatic Tunnel Addressing Protocol (ISATAP) address on the Automatic Tunneling Pseudo-Interface. The link-local ISATAP address has the form
FE80::200:5EFE:w.x.y.x or FE80::5EFE:w.x.y.x, in which w.x.y.x is an IPv4 address.To specify your IPv6 address parameters in Windows, click the System Menu, Control Panel, Network and Sharing Center, and then Change Adapter Settings. Now right-click your network interface and choose Properties. Highlight ‘Internet Protocol Version 6 (TCP/IPv6)’ and click Properties.


.
Be sure to have a look at the ‘IPv6 and Microsoft’ links below.
↑ Up to page menu
Further reference
General IPv66deploy.eu, Collection of IPv6 tutorials in PDF format
Afrinic.net, IPv6 virtual lab
Brighttalk.com, IPv6 on your network (webcast)
CIO.gov, Planning guide/roadmap toward IPv6 adoption within the U.S. government
Code.google.com, IPv6gen prefix generator
Deepspace6.net, ipv6calc
GetIPv6.info (ARIN), IPv6 presentations and documents
Google.com, IPv6 adoption statistics
HE.net, Porting applications from IPv4 to IPv6/IPv4 dual stack
Hpc.hpcmo.mil, Lessons learned after deploying IPv6 (from multiple organizations)
Icann.org, Testing firewalls for IPv6 and EDNS0 support
InfoSecInstitute.com, IPv6 surface analyzer
Internet2.edu, Internet2 IPv6 Working Group
Internetsociety.org, Deploy360 IPv6 resources
Ipbcop.org, Recommendations for IPv6 subnetting guidelines
IPv6tf.org, IPv6 For All (PDF; contains numerous real world examples of configuring IPv6 on various technologies)
IPv6-test.com, IPv6 connectivity test
Isc.sans.edu, IPv4-to-6to4 converter
Networkworld.com, IPv6 networking certifications
Networkworld.com, What if IPv6 fails to catch on?
Routermeister.net, Sipcalc IPv6 subnet calculator
Sixxs.net, Table comparing IPv6 transition methods
Sourceforge.net, HaCi IPv6 address administration tool
Surfnet.nl, Preparing and IPv6 addressing plan
Test-ipv6.com, IPv6 connectivity test
Wikipedia.org, Collection of IPv6 Address Management (IPAM) tools
Youtube.com, DEFCON 18: Who cares about IPv6?
IPv6 and security
Brighttalk.com, IPv6 requires fundamental change to vulnerability management programs (webcast)
Brighttalk.com, IPv6 – security threat or stronger defenses? (webcast)
InfoSecInstitute.com, SLAAC attack on Windows default IPv6 configuration
InfoSecInstitute.com, Security vulnerabilities of IPv6 tunnels
NIST.gov, Special Publication (SP) 800-119, Guidelines for the secure deployment of IPv6 (PDF)
Technet.microsoft.com, IPv6 security considerations and recommendations
Youtube.com, Recent advances in IPv6 insecurities
IPv6 and Cisco
Cisco.com, Enterprise IPv6 solution data sheets, presentations, and white papers
Cisco.com, IPv6: A service provider view in advancing MPLS networks
Cisco.com, IPv6 access control lists (ACLs)
Cisco.com, IPv6 network mobility
Cisco.com, IPv6 site multihoming
Cisco.com, IPv6 worldwide adoption statistics
Proprofs.com, CCNA IPv6 flash card questions
IPv6 and Linux
HE.net, Essential IPv6 for Linux system administrators (PDF)
Linux.com, IPv6 crash course for Linux and Another IPv6 crash course for Linux
TLDP.org, Linux IPv6 HOWTO
Youtube.com, Essential IPv6 for Linux system administrators (video)
IPv6 and Microsoft
Technet.microsoft.com, Changes to IPv6 in Windows Vista and Windows Server 2008
Technet.microsoft.com, How IPv6 works
Technet.microsoft.com, IPv6 for Windows frequently asked questions (FAQs)
Technet.microsoft.com, IPv6 forum
Technet.microsoft.com, IPv6 survival guide
Technet.microsoft.com, Support for IPv6 in Windows Server 2008 R2 and Windows 7
Zdnet.com, Windows 8 moves to IPv6 Internet
Notable IPv6-related IETF Requests For Comments (RFCs)
RFC 2080, RipNG for IPv6
RFC 2460, Internet Protocol Version 6 Specification
RFC 2461, Neighbor Discovery for IP Version 6 (IPv6)
RFC 2462, IPv6 Stateless Address Autoconfiguration
RFC 2473, Generic Packet Tunneling in IPv6 Specification
RFC 2528, Transmission of IPv6 over IPv4 Domains without Explicit Tunnels
RFC 3056, Connection of IPv6 Domains Via IPv4 Clouds (6to4)
RFC 3152, DNS Extensions to Support IP Version 6
RFC 3162, RADIUS for IPv6
RFC 3315, Dynamic Host Configuration Protocol Version 6
RFC 3375, Mobility Support in IPv6
RFC 3587, IPv6 Global Unicast Address Format
RFC 4007, IPv6 Scoped Address Architecture
RFC 4038, Application Aspects of IPv6 Transition
RFC 4213, Basic Transition Mechanisms for IPv6 Hosts and Routers
RFC 4291, IP Version 6 Addressing Architecture
RFC 4294, IPv6 Node Requirements
RFC 4380, Teredo: Tunneling IPv6 over UDP through Network Address Translations (NATs)
RFC 4862, IPv6 Stateless Address Autoconfiguration
RFC 5156, Special-Use IPv6 Addresses
RFC 5214, Intra-Site Automatic Tunnel Addressing Protocol (ISATAP)
RFC 5340, OSPF for IPv6
RFC 5533, Shim6: Level 3 Multihoming Shim Protocol for IPv6
RFC 5881, BFD for IPv4 and IPv6 (Single Hop)
RFC 5902, IAB Thoughts on IPv6 Network Address Translation
RFC 5952, A Recommendation for IPv6 Address Text Representation
RFC 5969, IPv6 Rapid Deployment on IPv4 Infrastructures (6rd)
RFC 5991, Teredo Security Updates
RFC 6052, IPv6 Addressing of IPv4/IPv6 Translators
RFC 6081, Teredo Extensions
RFC 6092, Recommended Simple Security Capabilities in Customer Premises Equipment (CPE) for Providing Residential IPv6 Internet Service
RFC 6144, Framework for IPv4/IPv6 Translation
RFC 6146, Stateful NAT64: Network Address and Protocol Translation from IPv6 Clients to IPv4 Servers
RFC 6177, IPv6 Address Assignment to End Sites
RFC 6296, IPv6-to-IPv6 Network Prefix Translation
RFC 6333, Dual-Stack Lite Broadband Deployments Following IPv4 Exhaustion
RFC 6540, IPv6 Support Required for All IP-Capable Nodes
RFC 6586, Experiences from an IPv6-Only Network
RFC 6724, Default Address Selection for Internet Protocol Version 6 (IPv6)
TERIMA KASIH ATAS KUNJUNGAN SAUDARA
Judul: IPv6: how and why it enables Internet evolution
Ditulis oleh Unknown
Rating Blog 5 dari 5
Semoga artikel ini bermanfaat bagi saudara. Jika ingin mengutip, baik itu sebagian atau keseluruhan dari isi artikel ini harap menyertakan link dofollow ke http://androidjapane.blogspot.com/2013/03/ipv6-how-and-why-it-enables-internet.html. Terima kasih sudah singgah membaca artikel ini.Ditulis oleh Unknown
Rating Blog 5 dari 5



0 komentar:
Posting Komentar